Traditional Breach and Attack Simulation (BAS) tools have provided organizations with a limited way (e.g., TTP coverage) to test their defenses against simulated attacks. However, SCYTHE is taking another step further by revolutionizing the BAS game with the introduction of 'smart tagging.' This innovative capability, linking proposed control to procedure, will change how adversarial emulation tests are developed and conducted, providing detection engineers and security operations teams with unprecedented insights and actions.
Rationale:
- Shortening the cycle to re-test (suggested detect rules: copy, paste, evaluate again) using internal resources moves us closer to continuous validation and away from the long intervals of pen testing.
- Automating one side of the feedback loop gives detection engineering professionals of all experience levels a productivity boost.
- Replaying existing campaigns in what-if scenarios allows one to gain a feel for the threshold of detection without increasing false positives. "Missed Detections" are not a negative experience overall.
The Limitations of Traditional BAS
Traditional BAS tools have offered a valuable service by allowing organizations to simulate attacks and test their defenses. However, these tools cannot provide detailed insights into the specific steps of an attack that the organization's security controls should detect. As a result, security teams are left to manually correlate test actions with security outcomes, which is time-consuming and prone to errors. Worse, teams are left with a false sense of security, feeling that they have covered all MITRE TTPs in a 'compliance'-like exercise but lack the realization (knowledge) of how real-world attacks work.
Introducing Smart Tagging: A Game-Changer for Adversarial Emulation
SCYTHE's 'smart tagging' feature transforms the way detection engineers (and red teams) approach validating security controls. This innovative capability allows engineers to directly link proposed/expected controls to a procedure, such as alerts or blocks triggered by an EDR or SIEM, within a SCYTHE emulation test. By leveraging smart tags and SIGMA rules, detection engineers can enrich tests with precise information on how the organization's security controls should detect specific actions. Better yet, teams benefit from the ability to reuse red team content with embedded detection actions, streamlining the process of security control validation and making it more efficient and effective.
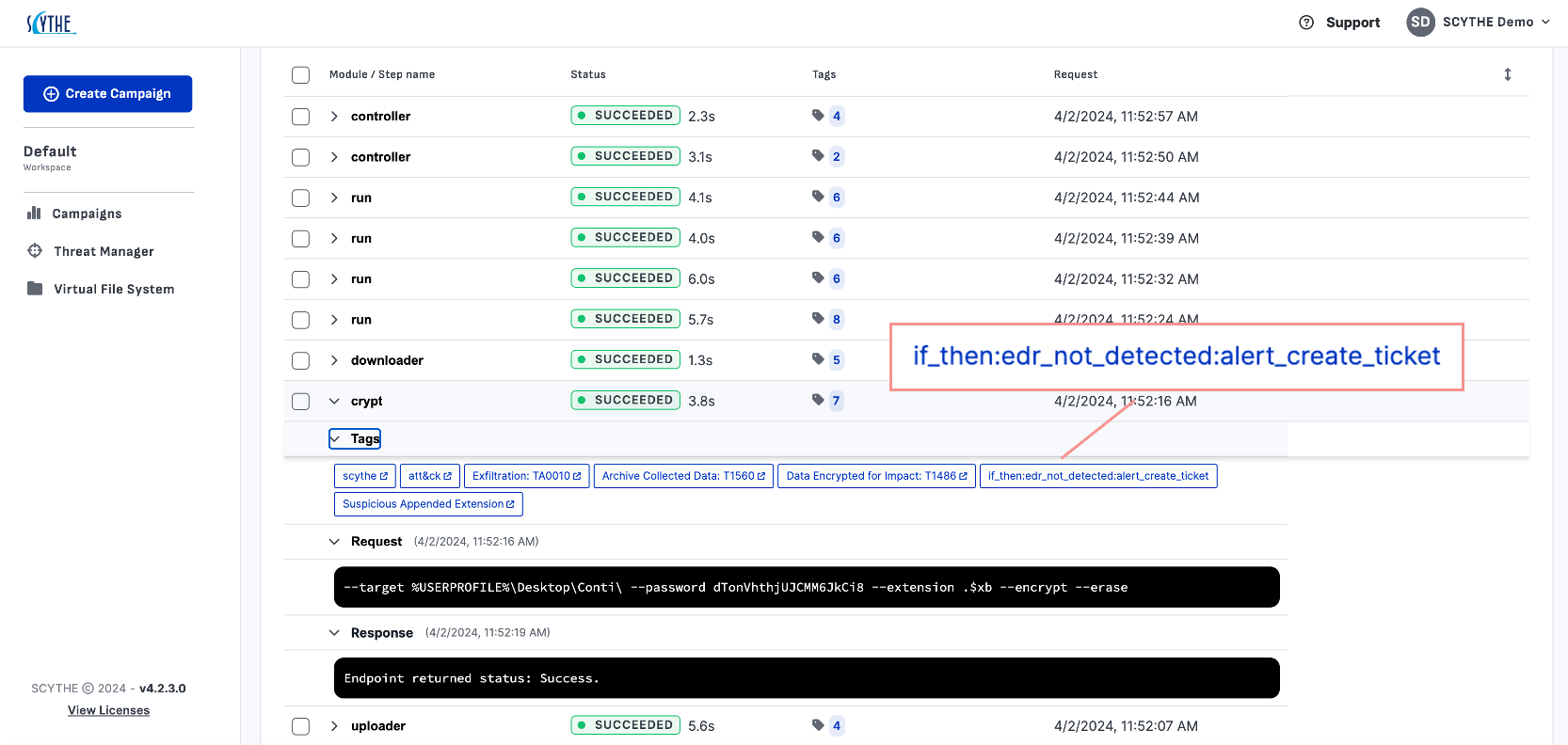
The smart tagging feature allows for a more nuanced and targeted approach to testing, as security teams can specify exactly which actions should trigger a detection (even specifying the detection via SIGMA rules). This level of granularity ensures that the organization's security controls are being tested in a way that closely mirrors real-world attack scenarios.
Automated Correlation and Ticket Creation
One of the most powerful aspects of SCYTHE's smart tagging is its ability to automatically inform the SCYTHE server to correlate test actions with security outcomes. This means that when the expected detection behavior deviates from what is specified in the smart tag, SCYTHE can automatically create tickets in systems like ServiceNow, Jira, etc. This automation ensures that the security team quickly identifies, assigns, evaluates, and mitigates gaps in the organization's security posture.
The automated ticket creation feature streamlines the process of managing and resolving security issues, reducing the time and effort required by security teams. It improves the organization's security operations' efficiency and enhances its overall security posture by ensuring that exposures are promptly addressed.
Empowering Detection Engineers and Security Operations
The introduction of smart tagging in SCYTHE's platform empowers red teams, detection engineers, and security operations teams to work together collaboratively. It provides them with a more precise and actionable way to test their security controls, as they can specify the exact conditions of an attack and the expected detection. This level of specificity is crucial for fine-tuning the organization's security measures and ensuring that they are effective against real-world threats.
Second, the automated correlation and ticket creation feature reduces the manual workload on security teams, allowing them to focus on more strategic tasks. By automating the process of identifying and addressing security gaps, SCYTHE helps organizations maintain a proactive stance in their cybersecurity efforts.=
Third, the ability to embed expected detections directly into the SCYTHE campaign ensures that the tests are aligned with the organization's security objectives. This alignment is critical to ensuring that the organization's defenses are robust and relevant to the specific threats it will potentially face.
Finally, the collective teams benefit from the initial investments made by their red team. By repurposing and augmenting existing red team emulations, everyone saves significant time. Better yet, emulation planning can be a more collaborative exercise, coupling the missions of the red and blue groups.
Conclusion
SCYTHE's introduction of smart tagging is set to further advance the BAS+ landscape by providing organizations with a more intelligent and efficient way to validate security controls, identify gaps, and provide mitigation guidance specific to a team's security stack. By enabling detection engineers and security operations teams to augment tests with expected detections and automating the correlation of test actions with security outcomes, SCYTHE empowers organizations to stay one step ahead of adversaries. As the cyber threat landscape continues to evolve, tools like SCYTHE that offer advanced capabilities and automation will be essential for maintaining a strong and effective cybersecurity posture.
Author Attribution:
Written by Marc Brown (@marc_r_brown), SCYTHE's VP of Product & Sales, a dynamic leader with diverse executive roles, startup enthusiast, lover of technology, innovation, and all things 'nerdy' cool.