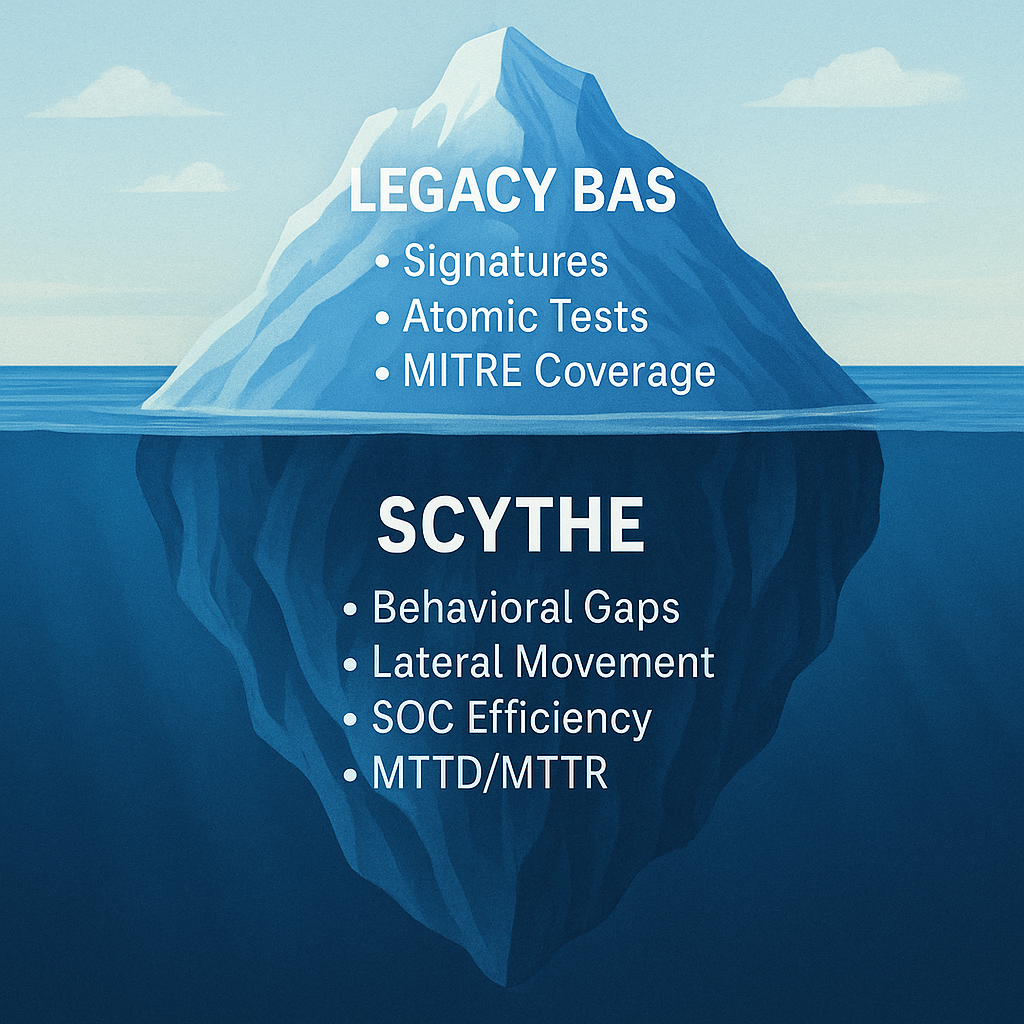
Legacy Breach and Attack Simulation (BAS) tools, such as those from Google Mandiant, AttackIQ and Picus Security, face significant technical challenges in fully supporting Adversarial Exposure Management (AEV) due to their reliance on signatures and Indicators of Compromise (IOCs).
These challenges stem from fundamental differences in approach compared to SCYTHE’s post-access multistage campaign emulation, which focus on the emulation of malicious behavior and derived actionable insights required by AEV and Continuous Threat Exposure Management (CTEM).
Below, I outline the key technical limitations of legacy BAS tools and contrast them with SCYTHE’s strengths.
1. Dependence on Signatures and IOCs Limits Realism
Challenge:
Legacy BAS tools often rely on predefined signatures and IOCs (e.g., known malware hashes, IP addresses, or file names) to simulate attacks. These are static and tied to specific, previously observed threats, making them less effective against novel or evolving attack techniques. Real-world adversaries frequently modify their Tactics, Techniques, and Procedures (TTPs) to evade signature-based detection, rendering IOC-based simulations outdated or incomplete.
Impact on AEV:
AEV requires emulating sophisticated, multistage attacks that mimic real-world adversary behavior across the entire kill chain (e.g., initial access, lateral movement, data exfiltration). Signature-based BAS tools struggle to replicate these dynamic, behavior-driven campaigns, leading to gaps in validating defenses against today’s highly creative adversaries.
SCYTHE’s Advantage:
SCYTHE’s platform focuses on emulating malicious behaviors, using frameworks like MITRE ATT&CK to map campaigns to real-world adversary actions. SCYTHE emulates attacks by precisely replicating the attacker's behavior, aiming to serve as a substitute for the actual attack.
SCYTHE emulates attacks by precisely replicating real adversary behavior, faithfully mirroring how threats unfold across the kill chain. This approach enables organizations to observe how multi-step attacks—like credential theft followed by lateral movement and discovery—would play out in their environment. Legacy BAS tools, by contrast, rely on chained micro-simulations of individual MITRE TTPs, treating each step in isolation. This oversimplified, static modeling fails to capture the complexity and context of real attacks. As a result, they often miss how benign-looking actions—when sequenced—can enable serious malicious outcomes, leaving blind spots where early indicators go undetected.
By emulating post-access, multistage attacks (e.g., privilege escalation, lateral movement), SCYTHE tests defenses under realistic conditions without relying on static IOCs. This behavioral focus aligns with AEV’s need for continuous, relevant testing.
2. Limited Scope Beyond Atomic Tests
Challenge:
Many legacy BAS tools excel at executing atomic tests—discrete, single-technique simulations (e.g., a phishing email or a specific exploit). While useful for validating individual controls, these tests fail to emulate complex, chained attack sequences that characterize real-world breaches. This fragmented approach misses critical interactions between attack stages, such as how staging data and bulk archiving behaviors almost always precede ransomware activity.
Impact on AEV:
AEV demands holistic validation across the attack lifecycle, including post-compromise behaviors. Legacy BAS tools’ focus on isolated tests limiting their ability to assess how security controls perform against coordinated, multistage campaigns, reducing their effectiveness in identifying systemic weaknesses.
SCYTHE’s Advantage:
SCYTHE’s AEV platform supports multistage campaign emulation, allowing red teams to design and execute complex attack flows that mirror real-world threats. Features like the Attack Flow Designer (introduced in SCYTHE 4.3) provide a visual interface to orchestrate campaigns, ensuring comprehensive testing and visual reporting across the kill chain. This capability directly supports AEV’s goal of continuous, end-to-end validation.
3. Scalability and Resource Intensity
Challenge:
Legacy BAS tools rely on widespread agent deployment to test and simulate attacks effectively. This approach results in complex deployment, high maintenance costs, increased network traffic, and performance degradation. For large enterprises, managing several agents is resource-intensive and impractical, particularly in hybrid IT/OT environments. Additionally, updating these agents further escalates operational costs. Companies must carefully plan and optimize agent deployment to balance attack surface coverage, control, and cost.
Impact on AEV:
AEV requires scalable, continuous testing to keep pace with evolving threats and dynamic environments. The resource-heavy nature of legacy BAS tools hinders their ability to adapt quickly, perform frequent, large-scale simulations, limiting their alignment with CTEM’s continuous validation phase.
SCYTHE’s Advantage:
SCYTHE employs an agentless model (using just-in-time compiled implants) to enable testing while reducing resource overhead, while offering optional agents for automated, continuous security control validation. SCYTHE’s agent-based approach involves targeted deployment on a limited number of endpoints, minimizing deployment time, resource usage, and maintenance efforts. This streamlined model allows enterprises to perform frequent, scalable attack emulations without overburdening IT or security teams, meeting the demands of Automated Emulation and Validation (AEV) for ongoing testing.
4. Inability to Adapt to Evolving Threats
Challenge:
Legacy BAS tools’ reliance on threat libraries built from known IOCs, defanged malware and signatures makes them slow to adapt to emerging threats. Updating these libraries requires manual intervention or vendor updates, which can lag behind the rapidly evolving threat landscape (e.g., new ransomware variants or APT TTPs). This reactive approach leaves organizations vulnerable to untested attack vectors.
Impact on AEV:
AEV emphasizes proactive identification and mitigation of vulnerabilities before exploitation. Legacy BAS tools’ delayed response to new TTPs undermines their ability to provide real-time insights into an organization’s exposure, a core requirement of AEV and CTEM.
SCYTHE’s Advantage:
SCYTHE integrates novel procedural (behavioral) techniques real-time from a variety of threat intelligence sources into our threat library. Additionally, SCYTHE enables customers to add in their own threat content based on the CTI. By leveraging MITRE ATT&CK and continuous updates (e.g., Threat Thursdays), SCYTHE ensures emulations reflect current adversary behaviors, enhancing AEV’s proactive stance.
5. Lack of Contextual and Actionable Insights
Challenge:
Legacy BAS tools often produce noisy, non-contextual results from their simulations, focusing on whether a control failed or succeeded without providing granular insights into why or how to remediate. This lack of prioritization based on business impact or exploitability hampers effective risk management.
Impact on AEV:
AEV requires actionable, prioritized findings that align with business objectives and risk profiles. Legacy BAS tools’ generic reporting limits their ability to guide remediation or demonstrate ROI to executives, a key aspect of CTEM’s validation and prioritization phases.
SCYTHE’s Advantage:
SCYTHE’s platform offers deep bi-directional integrations with SIEM, EDR, and ITSM platforms, enabling extensive data correlation and enhanced visibility into security control performance and efficacy. These integrations deliver actionable remediation insights, dashboards and risk reports. Additionally, features like the Vulnerability Management Validation MVP (SCYTHE 4.3) provide a Harvest Score to prioritize vulnerabilities based on real-world impact.
6. Limited Collaboration Across Teams
Challenge:
Legacy BAS tools are often designed for siloed use by blue teams, with limited integration for blue or purple team collaboration. This restricts their ability to foster unified security efforts, as defensive teams may not have access to simulation results or the ability to refine detection rules in real time.
Impact on AEV:
AEV relies on collaborative exercises (e.g., purple teaming) to align offensive and defensive strategies. Legacy BAS tools’ lack of collaborative features hinders their ability to drive iterative improvements across people, processes, and technology, a cornerstone of AEV.
SCYTHE’s Advantage:
SCYTHE emphasizes purple teaming and cross-team collaboration through features like in-platform messaging, shared dashboards, and Managed Purple Team Services. These capabilities ensure red and blue teams work together to validate controls and improve resilience, directly supporting AEV’s holistic approach.
Conclusion
Legacy BAS tools, built on signatures, IOCs and micro-simulations, who’ve stressed the importance of email, WAF, and initial access support for years, face critical technical challenges in supporting AEV due to their limited realism, scope, scalability, adaptability, and collaboration features.
These shortcomings make them less effective at meeting the demands of AEV and CTEM, which require continuous, behavior-driven validation across the full attack lifecycle.
In contrast, SCYTHE’s post-access multistage campaign emulation overcomes these limitations by prioritizing post-access malicious behavior, leveraging real-time threat intelligence, and enabling scalable, collaborative, and actionable testing. This positions SCYTHE as a leader in delivering the proactive, comprehensive validation needed for modern cybersecurity resilience.