Have you ever wondered if you could catch malicious actors if they got past defenses? Perhaps you’d like to catch ransomware actors before they exfiltrate your data and deploy the ransomware payload. Often actors use similar behaviors across breaches due to training, habits, experience, and manuals. These behaviors, also called procedures, are the perfect opportunities to alert on indicators of attack (IOAs), before attackers can cause impact. This walkthrough will cover how SCYTHE makes cyber threat intelligence (CTI) actionable for defenders.
SCYTHE allows procedure-level intelligence to be actionable by testing alert capabilities in your unique security stack. The example below shows an EDR evaluation for the first stage of a Conti Ransomware attack leveraging IcedID as the initial command and control (C2). This beginning stage of the attacker's intrusion is crucial for defenders to detect, as it enables responders to contain a breach swiftly and prevent impact.
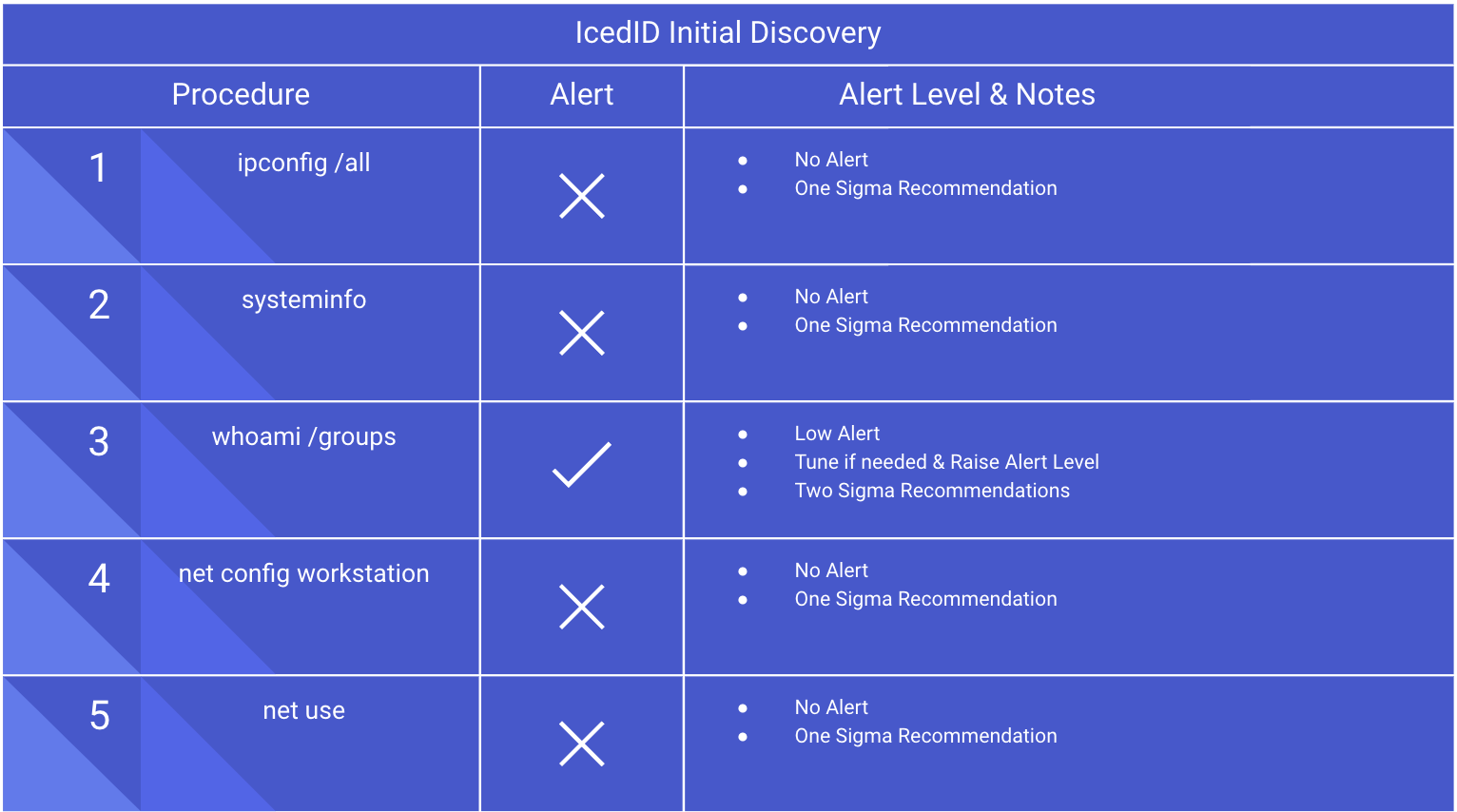
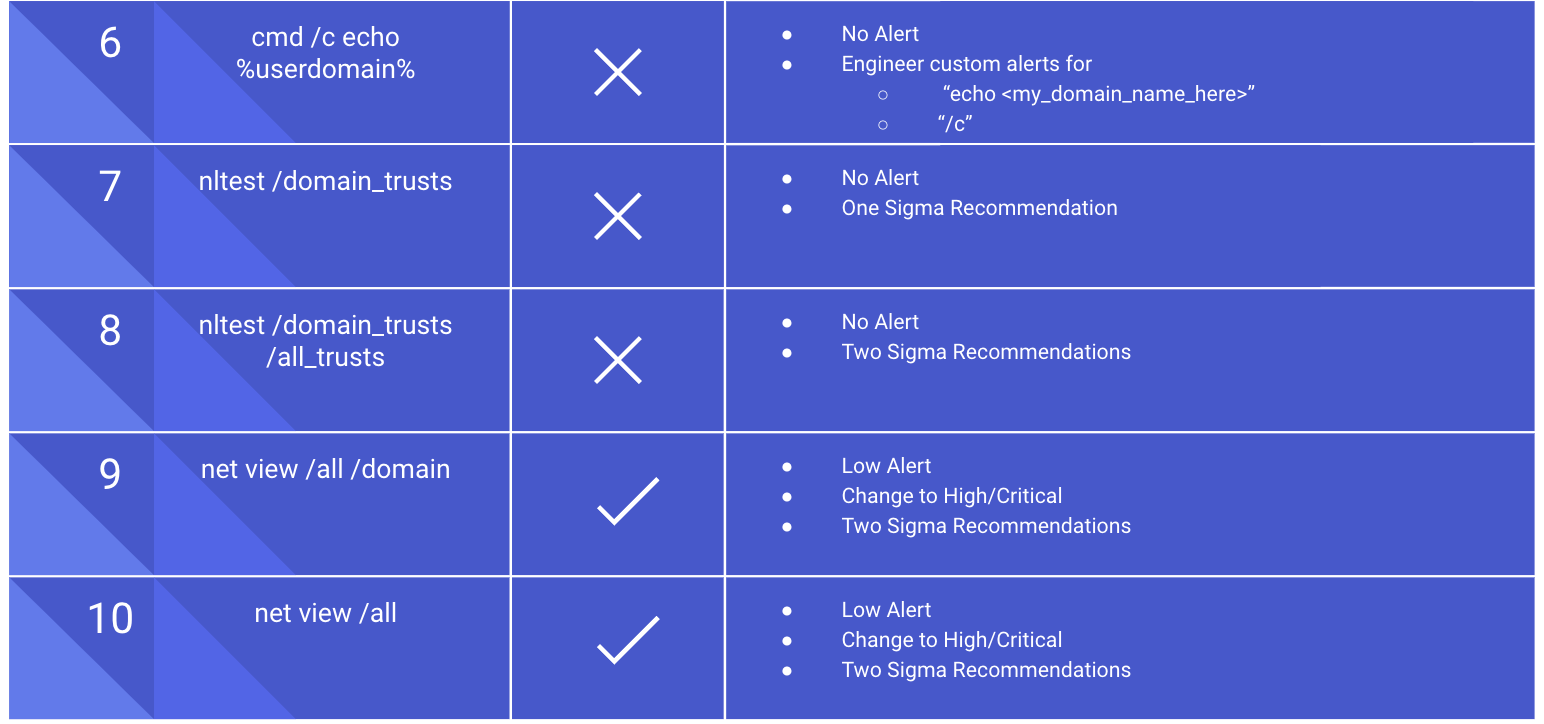
Notice how all the EDR alerts are "Low" level alerts. Many organizations do not have the resources to investigate low alerts unless they are correlated with an investigation. Therefore, changes in detection and alerting capabilities are necessary for ensuring a SOC response is taken and reducing the mean time to detect.
The first step for defenders is to review the alerts that already cover emulated procedures. By analyzing each specific alert’s count over a set of time, we can quickly recommend alerts to elevate to a higher level with minimal or no tuning. Conducting this tuning of alerts to a higher level guarantees SOC analysis and investigation, which drives better mean time to detect and response metrics. If the alert count is high, more resources will be needed for further tuning or custom detection engineering. If there are no alerts for the procedure, then Sigma recommendations are an excellent starting point to increase detection capability and reduce the mean time to detect. In today's threat landscape, alert tuning and detection engineering is crucial for defending against modern threats, including living-off-the-land techniques.
There are discussions around solely using correlation for alerting, but that approach has gaps. Correlation is an excellent capability but needs to be paired with well-tuned alerting to operate efficiently. Correlation is often easily broken by changing a few procedures or increasing the timing between steps. Relying solely on correlation instead of a combination of tuning and engineering procedure-level alerts often results in lower detection coverage.
In closing, organizations must test their unique security stack for known adversarial actions. Emulation testing allows for evaluating what triggers human analysis by a security analyst. Measuring alert coverage is a crucial first step in tuning alerts, engineering new ones, and driving down the mean time to detect.
