Ego does not drive risk assessments; business does. The old days of doing whatever it took to win or exploring “fun” technical exploitation techniques independent of what drives business value are over. Cybersecurity risk assessments need to be grounded in identifying, assessing, and prioritizing risks that can have a material impact on business operations. But, there is a spectrum of different approaches that provide different levels of value, albeit linked to an organization's security maturity. As the team's capabilities increase, more advanced assessments will be essential.
Bryson's Attack Model™ (aka "BAM")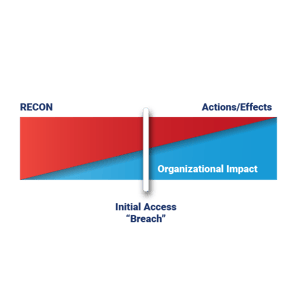
Lockheed Martin’s Killchain. MITRE ATT&CK. And more. All models describe the phases of any threat campaign in different ways.
I simplify these into three phases that illustrate the critical components while understanding them in the context of organizational impact.
System | System of Systems
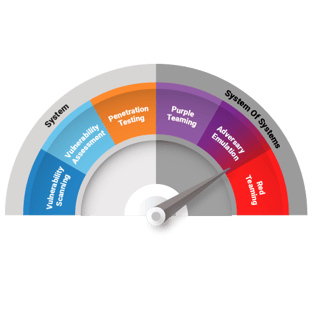
Vulnerability Scanning
Scanning an organization for vulnerabilities with an automated scanner is the simplest of ethical hacking assessments an organization should perform. The goal is to inventory and identify known vulnerabilities in target systems and applications. This step requires minimal effort as long as the proper tools are in place.
Vulnerability Assessments
After a vulnerability scan is completed, an ethical hacker can validate the vulnerabilities manually to remove false positives and calculate an accurate risk rating. Vulnerabilities are assigned a Common Vulnerabilities and Exposure (CVE) ID and scored with the Common Vulnerability Scoring System (full disclosure: Jorge Orchilles, Advisory Council, was a working group voting member for the current version CVSSv3.1).
Penetration Testing
Penetration Testing (pen-testing) has several definitions. The most common is the annual test compliance requirement, which could cover any of the following exercises in this next section. For our purposes here, we define Penetration Testing as emulating unauthorized system access through exploitation or configuration error. This is the main differentiator from vulnerability assessment, where vulnerabilities are only being verified. Penetration Testing involves exploiting vulnerabilities, configuration errors, or authentication under controlled circumstances in a professional, safe manner according to a carefully designed scope and Rules of Engagement. Penetration Testers often find vulnerabilities not known by the vendor or defenders and focus on bypassing preventive controls. An example of a penetration test is GRIMM's work to identify vulnerabilities in DJI drones.
System of Systems Focus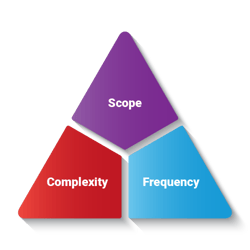
The next set of approaches advance by examining the complex systems environment of your organization, considering account interconnectivity and beyond prevention to incorporating detection and response into your evaluation.
There are three variables to these exercises:
Scope
What are we including in the scope of the test? Start small. A lot can be learned from looking at even just one computer with a gold image in a lab.

Complexity
Offensive tools have to balance across diametric requirements of convenience and realism. The more convenient the tool is, generally the less realistic it is; for example, if I'm automatically mapping and simulating exploitation to create attack graphs, that is convenient, but it's not realistic. Furthermore, deeper complexity/realism generally requires specialized offensive talent or a 🦄 level tool.
Frequency
How often do we run exercises? Generally speaking, the aspirational goal is to work up to quarterly exercises, but there is no one answer, and it depends on multiple organizational factors (staffing, leadership support, exercise/process maturity, (OG&E example of daily testing vs full exercise).
Purple Team Exercises
A Purple Team is a collaborative, milestone-driven exercise that is, at a minimum, a virtual team of Red capabilities (you don't have to have a Red Team, just what's needed to drive the offensive behaviors) and the Blue Team (Ops). It can also incorporate other functional areas, such as including HR, for a PII exercise.
A Purple Team Exercise is an open engagement where collaboration, execution, and remediation of the attack activity is managed with the Blue Team as it occurs. Purple Team Exercises are "hands-on keyboard" exercises where Red and Blue teams work together with an open discussion about each attack technique and defense expectation to improve people, processes, and technology in real time. Purple Team Exercises are Cyber Threat Intelligence led, emulating Tactics, Techniques, and Procedures (TTPs) leveraged by known malicious actors actively targeting the organization to identify and remediate gaps in the organization's security posture.
Red Teams use SCYTHE to create the payloads for the selected TTPs. They are able to consistently and effectively execute the same TTP as many times the Blue Team requires to tune their defenses in real time. As the industry leader in purple teaming, SCYTHE published the Purple Team Exercise Framework (PTEF).
Adversary Emulations
Adversary emulation is an ethical hacking engagement where a Red Team imitates how an attacker operates, leveraging frameworks like MITRE ATT&CK to identify specific tactics, techniques, and procedures (TTPs) that a real threat actor might use against an organization. Rather than focusing on attacks less likely to occur, these engagements draw upon Cyber Threat Intelligence to identify adversaries with the intent, opportunity, and capability to attack. Adversary Emulations may be performed in a no-knowledge (Red Team Engagement) or full-knowledge (Purple Team Exercise). SCYTHE introduced #ThreatThursday, where cyber threats are assessed, dissected, and analyzed. Every week, SCYTHE selects a new adversary, consumes the latest Cyber Threat Intelligence, and creates a thorough adversary emulation plan. It's all shared on our social channels and website and is open for all SCYTHE platform users to explore.
Red Team Engagements
You’ve reached the summit of your first mountain. Consistent purple team exercises have established a foundation of visibility, protection, and detection in the organization. Now you’re ready to climb the pinnacle of risk assessments, taking red capabilities to the next level: the organization looks to human operators using the art and imagination of the possible to find the fish tank (i.e., Casino Gets Hacked Through Its Internet-Connected Fish Tank Thermometer). The main customers are the defenders who focus on detection (response) and preventative controls (protection). The Red Team emulates the Tactics, Techniques, and Procedures (TTPs) of adversaries to test an organization holistically. As an enterprise red team tool and command and control (C2) framework, SCYTHE allows the Red Team to focus on emulating attack behaviors and custom TTPs instead of maintaining and troubleshooting the tools themselves and supports the process, communication, and replayability of the exercise. SCYTHE is a Red Team force multiplier.
.jpg?width=352&name=5f21b3a2f585b4864807e770_kevin-ku-w7ZyuGYNpRQ-unsplash%20(1).jpg)