
#ThreatThursday - Egregor Ransomware
Happy New Year Threat Thursday readers! New year, new attacks? Not quite. Ransomware continues to be leveraged by threat actors to monetize their ...
Jorge Orchilles

Happy New Year Threat Thursday readers! New year, new attacks? Not quite. Ransomware continues to be leveraged by threat actors to monetize their criminal activity. This week we will take a look at Egregor ransomware that has breached, exfiltrated data, and brought down multiple networks since September 2020. Stealing data before deploying ransomware has been a common modus operandi of the Egregor group. This provides more leverage for the threat actor and helps to achieve their overall objective: getting paid by executing “double-extortion” similar to Ryuk and Maze. It is important to understand these adversary behaviors, how to test our organization against these TTPs, and to better detect and respond to these attacks before they start costing money. Now, let’s dive into this together.
Cyber Threat Intelligence
After researching this threat group and ransomware, we found that Egregor has been responsible for other high profile attacks on multiple organizations: TransLink, Crytek, Ubisoft, Cencosud, and Barnes and Noble. These attacks provide enough data for us to understand how this threat actor operates. Here’s a shout out to some excellent companies and analysts that were willing to share their findings with the community:
- https://news.sophos.com/en-us/2020/12/08/egregor-ransomware-mazes-heir-apparent/
- https://www.recordedfuture.com/egregor-ransomware-attacks/
- https://www.bankinfosecurity.com/qbot-banking-trojan-now-deploying-egregor-ransomware-a-15430
- https://www.digitalshadows.com/blog-and-research/egregor-the-new-ransomware-variant-to-watch/
- https://www.trendmicro.com/en_us/research/20/l/egregor-ransomware-launches-string-of-high-profile-attacks-to-en.html
- https://blog.malwarebytes.com/ransomware/2020/12/threat-profile-egregor-ransomware-is-making-a-name-for-itself/
FBI Alert:
Based on cyber threat intelligence, Egregor has not been too innovative in comparison to the other Ransomware we have covered in previous Threat Thursdays. The only exception is their requiring of a password to decrypt the malware prior to execution of (T1480 - Execution Guardrails) that we previously covered. This is also a feature of the SCYTHE platform. It is believed by some intelligence providers that Egregor actors share the same operators as Maze given Egregor attacks started at the same time Maze was shut down. There is similarity of exfiltrating data before encrypting to perform “double extortion” (naming and shaming the victim organization apart from ransom). The group hosts “Egregor News” as an extortion site to increase pressure and obtain payment. However, according to a Bankinfosecurity article, QakBot operators have abandoned ProLock for Egregor ransomware. This means that a possible combination of Maze and QakBot operators may be working together. Their analysis shows the TTPs used by the threat actors in Egregor attacks are almost identical to the ones used by the ProLock operators.
Egregor group performs the following at a high level:
- Initial access is obtained via phishing emails with attachments leveraging the well-known Qbot/Qakbot.
- The malware checks the “Default Language ID” of the victim system and user account. If the language is any of the following, it exits and does not execute: Uzbek, Romanian, Azerbaijani, Turkmen, Georgian, Kyrgz, Ukrainian, Kazakh, Tatar, Russian, Tajik, Armenian, Belarusian, Romanian.
- Egregor does not have the capability to move laterally on its own. It leverages manual operation from egregor threat actors.
- Collects victim system information, including username, computer name, general system information, domain name, workgroup, and installed AV programs (such as Windows Defender).
- Deletes shadow copies using WMI.
- Creates a LNK file: <8 characters>.lnk file in each encrypted directory.
- Creates %ProgramData%\dtb.dat: this file name was also used in Sekhmet ransomware.
- Exfiltrated data for extortion.
- Encrypts a wide variety of data files, including images, videos, documents, SQL and other database-related files, Web pages, JavaScript files, and executables.
- Egregor drops a ransom demand in a text file named RECOVER-FILES.txt , similar to Sekhmet ransomware.
- The ransomware note has been seen to be sent to all printers connected to each machine as shown in FIgure 1.

Adversary Emulation Plan
We have shared this adversary emulation plan in our Community Threats GitHub, which happens to be the largest public library of adversary emulation plans. In addition, we shared a MITRE ATT&CK Navigator layer for planning purposes. Below is the Egregor Threat Profile:
Import the Egregor threat into SCYTHE’s Threat Manager and then click Threat Catalog. Scroll to the Egregor threat and click to see the adversary emulation plan step by step and click “Create Campaign from Threat”.
Name the campaign and follow along to customize it for your environment with execution guardrails and defense evasion through rundll32.exe (just like Egregor executes in the wild).
| Tactic | Description |
| Description | Egregor is an opportunistic group and does not focus on specific industries or geographic regions. Targets are based on accessibility, opportunity, and company’s revenue. Previous targets have been schools, manufacturers, logistics organizations, financial institutions, and technology companies. |
| Objective | “Double-extortion” via exfiltration of data for extortion and ransoming data for payment. |
| Command and Control | T1071.001: Application Layer Protocol: Web Protocols (HTTPS) T1573: Encrypted Channel |
| Initial Access | T1566: Phishing - Qbot (also known as Qakbot) deploys from a malicious document file attached to an e-mail message |
| Execution | T1204.002: User Execution: Malicious File T1053.005: Scheduled Task/Job: Scheduled Task T1059.001: Command and Scripting Interpreter: PowerShell |
| Defense Evasion | T1218.001: Signed Binary Proxy Execution: Rundll32 T1480: Execution Guardrails: DLL will only execute when given a password as a command line parameter |
| Discovery | T1087: Account Discovery T1082: System Information Discovery T1057: Process Discovery T1518.001: Software Discovery: Security Software Discovery |
| Collection | T1113: Screen Capture |
| Lateral Movement | Egregor has no way to spread itself. Therefore, it requires the attackers to move laterally themselves, using built-in Windows capabilities and other exploitation tools. |
| Exfiltration | T1041: Exfiltration Over C2 channel |
| Impact | T1486: Data Encrypted for Impact T1485: Data Destruction T1490: Inhibit System Recovery T1489: Service Stop |
Execution Guardrails
Once you have named the campaign, proceed to adding execution guardrails by restricting the campaign per device, domain, and start and end dates:
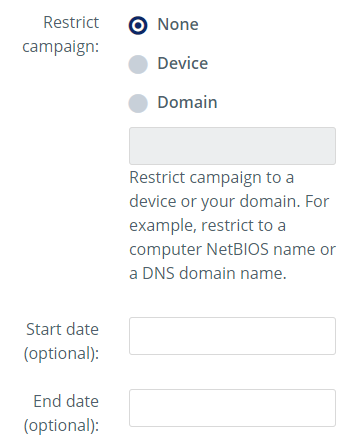
Begin the campaign once you have set your device or domain information so that Egregor only executes in your target environment. Now, download the stager as a DLL.
The synthetic ransomware will be executed just like the Egregor threat actors execute their ransomware:
- Open a cmd.exe and navigate to the location of the DLL
- rundll32.exe egregor.dll,PlatformClientMain
The execution of the Egregor campaign will begin following the adversary emulation plan.
System Default UI Language
If the victim system’s language is any of the following, Egregor does not execute: Uzbek, Romanian, Azerbaijani, Turkmen, Georgian, Kyrgz, Ukrainian, Kazakh, Tatar, Russian, Tajik, Armenian, Belarusian, Romanian.
Creating detection may be valuable to your organization, and there are multiple ways to check the default language:
Registry:
- reg query
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Nls\Language
Powershell:
- Get-Culture
- Get-Culture | Format-List -Property *
- [CultureInfo]::InstalledUICulture
cmd.exe requires elevation:
- dism /online /get-intl
Emulating Ransomware
Is it possible to emulate ransomware? Of course! SCYTHE users can emulate ransomware without introducing risk to the target organization. The secret is to avoid encrypting or destroying production data. Instead, SCYTHE will create new files in order to execute the typical ransomware steps of exfiltrating, encrypting, and downloading a ransom note. This method ensures no data or systems are impacted and business can continue on as normal.
Defend against Ransomware
Like all ransomware, these threats require a defense in-depth approach to prevent initial access from Qakbot phishing emails. It is important to focus on detecting the adversary behaviors prior to the ransomware execution. Once the ransomware executes, it will reach its objective in minutes. This educates employees on the impact of ransomware by emulating these attacks right in front of them. This will go a long way by showing what could possibly come against your organization.
Given that the group behind Egregor claims to sell stolen data if ransoms are not paid, it’s not enough to only have good backups of data as a mitigation for ransomware. Organizations need to assume that their data has been breached if they suffer an Egregor attack.
The FBI alert for Egregor provides the following, generic guidance:
- Back-up critical data offline.
- Ensure copies of critical data are in the cloud, on an external hard drive, or storage device.
- Secure back-ups. Ensure data is not accessible for modification or deletion from the system where the data resides.
- Install and regularly update anti-virus or anti-malware software on all hosts.
- Use secure networks only. Avoid using public Wi-Fi networks.
- Use two-factor authentication and do not click on unsolicited attachments or links in emails.
- Prioritize patching of public-facing remote access products and applications, including recent RDP vulnerabilities (CVE-2020-0609, CVE-2020-0610, CVE-2020-16896, CVE-2019-1489, CVE-2019-1225, CVE-2019-1224, CVE-2019-1108).
- Review suspicious .bat and .dll files, files with recon data (such as .log files), and exfiltration tools.
- Securely configure RDP. Restrict access by using multi-factor authentication or strong passwords.
Conclusion
The start of this new year has brought more sophisticated ransomware attacks against corporations. Egregor actors appear to be connected to Maze, which has been shut down, and Qakbot. The operators are leveraging a new malware that is similar to Sekhmet. This is clear evidence that the threat actors continue to evolve and leverage their previous work. To successfully defend against these attacks, we must emulate the real adversary behavior in our environments to test, measure, and improve our people, process, and technology (security controls). Adversaries will continue to evolve and it is critical that we also adapt quickly in order to defend against the latest attacks.
This Threat Thursday post discusses active research by SCYTHE and other cited third parties into an ongoing threat. The information in this post should be considered preliminary and may be updated as research continues. This information is provided “as-is” without any warranty or condition of any kind, either express or implied.
About SCYTHE
SCYTHE provides an advanced attack emulation platform for the enterprise and cybersecurity consulting market. The SCYTHE platform enables Red, Blue, and Purple teams to build and emulate real-world adversarial campaigns in a matter of minutes. Customers are in turn able to validate the risk posture and exposure of their business and employees and the performance of enterprise security teams and existing security solutions. Based in Arlington, VA, the company is privately held and is funded by Gula Tech Adventures, Paladin Capital, Evolution Equity, and private industry investors.
Latest Posts
Related Threat Thursday


Threat Thursday Top Ransomware TTPs
Top Ransomware TTPs At SCYTHE we are constantly collaborating with industry experts and...

#ThreatThursday - Ryuk
Welcome back to another SCYTHE #ThreatThursday! This week, we take a deeper dive into emulating and...






