Why Legacy BAS Vendors Fall Short in Adversarial Exposure Validation
In the complex ecosystem of cybersecurity analysts, vendors, and techniques, Continuous Threat Exposure Management (CTEM) has emerged as a solid ...
Marc Brown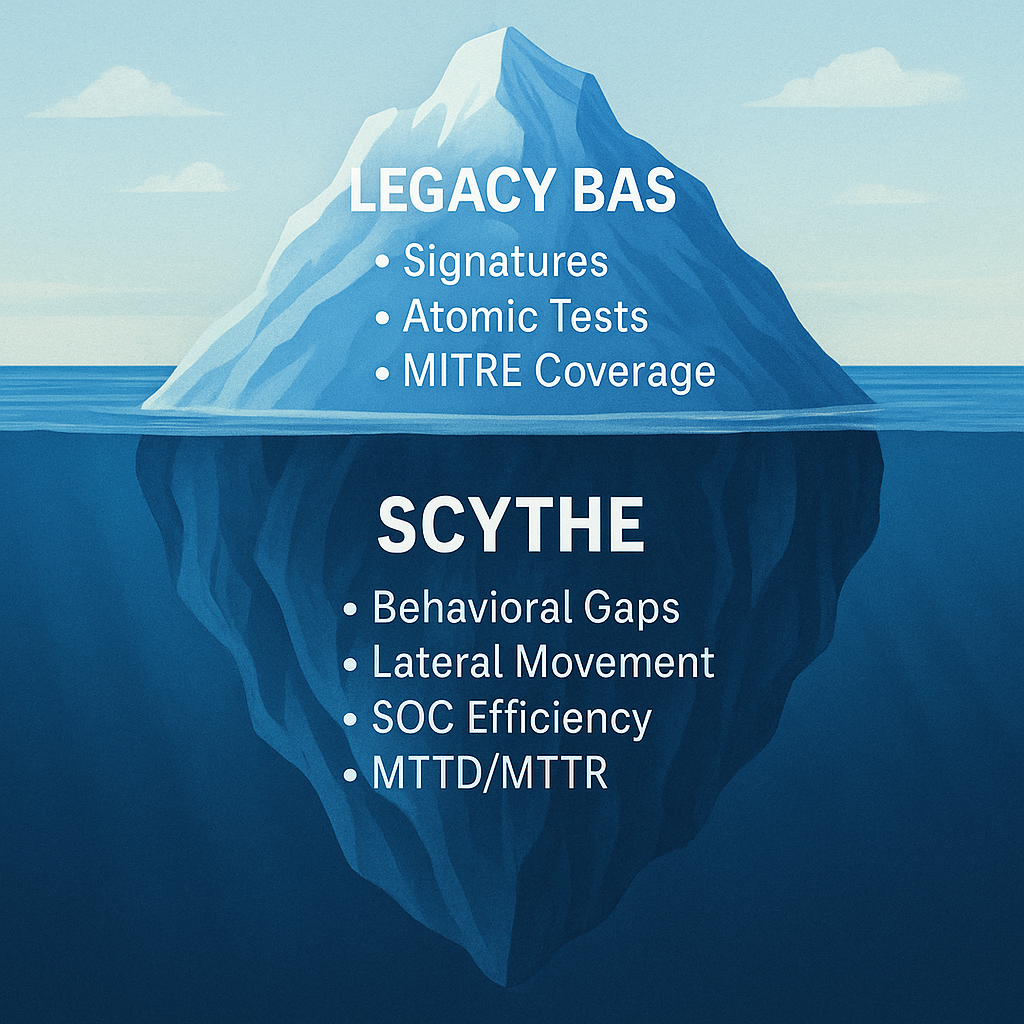
In the complex ecosystem of cybersecurity analysts, vendors, and techniques, Continuous Threat Exposure Management (CTEM) has emerged as a solid strategy for proactive defense, with Adversarial Exposure Validation (AEV) at its core. AEV demands realistic, multi-stage attack emulations to test and validate security controls against real-world threats, with a significant focus on malicious behavior. Yet, many legacy Breach and Attack Simulation (BAS) vendors are rebranding themselves as AEV platforms, claiming to meet these demands. SCYTHE, a leader in adversarial emulation, asserts that these legacy BAS platforms are technically ill-equipped to deliver true AEV due to their outdated, simulation-based approaches. Here’s why their claims don’t hold up and how SCYTHE’s behavior-focused, multi-stage emulation sets the standard.
The Legacy BAS Shortfall: A Flawed Foundation
Core Metrics: Where Legacy BAS Fails
AEV requires robust metrics to measure security posture, guide remediation, and demonstrate compliance. Legacy BAS platforms, tethered to their simulation-based roots, struggle to deliver the depth and accuracy needed for these metrics. SCYTHE’s platform, designed for adversarial emulation, excels in providing actionable, evidence-based insights. Let’s break down the key metrics and why legacy BAS falls short:
1. Detection Coverage and Fidelity
Legacy BAS tools offer broad detection coverage by simulating a wide range of individual MITRE ATT&CK TTPs, but their fidelity is limited due to reliance on scripted, atomic actions that lack environmental awareness and behavioral realism. These tools often simulate isolated techniques without chaining them into multi-step attack paths, resulting in outputs that may not reflect how real adversaries operate. As a result, the detections they generate can be overly simplistic and lack contextual accuracy, reducing their value for tuning defenses targeting malicious behavior.
In contrast, SCYTHE delivers high-fidelity adversary emulation by executing realistic attack chains that mirror actual adversary behavior, adapting to the production environment and generating true-positive detections. SCYTHE’s approach ensures security teams gain both deep coverage across the kill chain and high-confidence alerts, improving detection effectiveness, response readiness, and alignment with real-world threats across both IT and OT/ICS systems.
By the way, pet peeve here, chasing "MITRE TTP coverage" as a metric is misleading and wasteful. Teams often burn countless hours and resources treating it like a checklist, focusing on techniques that may be irrelevant to their actual threat landscape. It creates a false sense of security—appearing comprehensive on paper while offering little real-world protection. Ultimately, it's a feel-good metric that masks business-needed operational gaps rather than addressing them.
2. Threat Preparedness
Measuring threat preparedness—specifically measuring an organization's ability to thwart a phishing, ransomware, and insider attack—is inherently challenging due to the multi-stage nature of these threats and the need to test both static and behavioral detections across people, processes, and tools.
Legacy BAS tools struggle here because they rely on atomic, isolated simulations that lack context and sequence. They cannot replicate how a phishing email leads to credential theft, privilege escalation, lateral movement, and ultimately data encryption or exfiltration. As a result, these tools produce overly simplistic assessments that miss critical detection and response gaps—particularly those tied to user behavior, control misconfigurations, coordination between security tools, and operations.Why this matters: a threat steals credentials to use them, not celebrate in their Operations Center and their activities will look different on your host and networks. If you're not detecting on this level, you're not going to detect much beyond your tests.
SCYTHE addresses these limitations by emulating real-world adversary behavior in full attack chains, enabling accurate measurement of how threats unfold in an organization’s specific environment. SCYTHE’s automated control validation rigorously tests security tooling, detection logic, and user-facing processes—such as lateral movement and SOC escalation workflows. This allows organizations to generate meaningful, outcome-driven threat preparedness scores that reflect not just whether a control exists, but whether it actually works in concert within their operations apparatus as intended when challenged by realistic adversary behavior. In doing so, SCYTHE reveals hidden risks and enables proactive improvements that reduce exposure and business impact.
3. Security Control Effectiveness
Legacy BAS tools offer only a narrow view of security control effectiveness, typically using static, pass/fail outcomes based on signature detection or predefined rule matches. These tools often fail to assess how controls perform against dynamic, evolving threats, providing limited insight into whether security technologies like EDR, SIEM, or SOAR can detect or respond to real adversary behaviors. As a result, organizations are left with incomplete data, unable to determine whether their defenses are truly working or how to improve them.
In contrast, SCYTHE delivers evidence-based, repeatable assessments that go beyond binary results. By emulating realistic adversary behavior and chaining TTPs across the kill chain, SCYTHE tests how controls behave in context—whether alerts are generated, detections logged, and automated responses triggered. These detailed metrics not only validate tool performance but also uncover misconfigurations, tuning gaps, and alerting blind spots. SCYTHE provides the clarity needed to demonstrate the ROI of existing security investments, identify underperforming tools, and prioritize optimization efforts. Unlike legacy BAS, SCYTHE offers a continuous, data-driven approach to validating and improving the actual effectiveness of your security stack.
4. Compliance Validation Status
Legacy BAS tools provide adequate support for compliance validation, providing checkbox-style assessments that confirm whether specific security controls exist or basic TTPs trigger expected alerts. Unfortunately, these tools often lack the depth to validate whether those controls are configured correctly, functioning as intended, or aligned with real-world threat scenarios. As a result, they fall short in demonstrating true compliance with evolving standards that demand evidence of operational effectiveness—such as NIST 800-53, TSA SD02C, or NERC CIP.
5. Mean Time to Detect and Respond (MTTD/MTTR)
Legacy BAS tools offer limited capability to measure Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), primarily because they simulate isolated, atomic actions that don’t reflect the full lifecycle of a real attack. Without emulating multi-stage adversary behavior or capturing how detections unfold over time, these tools cannot accurately assess how long it takes for security teams to detect, investigate, and respond to a live threat. As a result, MTTD and MTTR metrics derived from legacy BAS tend to be incomplete, artificial, or disconnected from operational reality.
SCYTHE, on the other hand, enables precise measurement of MTTD and MTTR by executing realistic, end-to-end attack campaigns in production-like environments.
6. SOC Efficiency (Visibility + Timing)
Legacy BAS tools provide a limited view of SOC efficiency because they focus on isolated, atomic simulations that don’t expose real gaps in visibility or measure how quickly a team responds to complex threats. These tools typically assess whether a specific signature triggered an alert, but fail to account for blind spots across network, endpoint, or cloud environments, and offer no insight into how alerts are triaged, escalated, or acted upon. As a result, they overlook the interplay between detection coverage and timing—two critical dimensions of SOC performance.
SCYTHE delivers a far more comprehensive assessment of SOC efficiency by emulating realistic, multi-stage attacks that traverse various layers of the environment. These adversarial campaigns test whether security controls detect activity at each stage, how alerts are prioritized, and how quickly the SOC responds. SCYTHE measures not only tool efficacy, but also human and process performance—providing a complete picture of how people, technology, and workflows interact under real pressure. This visibility enables organizations to identify bottlenecks, reduce alert fatigue, and allocate resources more effectively, ultimately driving faster, more informed incident response and improving overall SOC efficiency.
7. Vulnerability Impact (Coming Soon)
Legacy BAS tools typically assess vulnerabilities based on static CVSS scores, which often fail to reflect real-world exploitability or operational risk. This approach can lead to misprioritization—focusing remediation on high-scoring vulnerabilities that may not be exploitable in the current environment, while overlooking lower-scoring issues that could enable actual attacker success. These tools rarely test how a vulnerability behaves when combined with lateral movement, privilege escalation, or other chained behaviors, limiting their ability to measure true business impact.
SCYTHE’s upcoming Harvest Score addresses this gap by dynamically adjusting Vulnerability Priority Ratings (VPR) based on actual exposure tests. Rather than relying solely on theoretical severity, SCYTHE evaluates how vulnerabilities perform in adversarial scenarios—whether they enable privilege escalation, persistence, or data access—providing a practical, evidence-driven measure of impact. This contextual scoring empowers teams to focus remediation efforts on vulnerabilities that pose the highest real-world risk, something legacy BAS tools simply aren’t built to do. SCYTHE’s approach bridges the gap between vulnerability management and threat-informed defense, ensuring resources are directed where they matter most.
The SCYTHE Difference: Adversarial Emulation Done Right
SCYTHE’s AEV platform is purpose-built for CTEM, offering unmatched flexibility and realism. Unlike legacy BAS, which tests one or a sequence of independent atomic tests, SCYTHE operates in production environments, emulating complex multi-stage campaigns. Our agentless deployment minimizes overhead, while seamless integrations with EDR, SIEM, SOAR, and ticketing platforms turn emulation data into actionable insights. Whether empowering red teams, validating blue team detections, or fostering purple team collaboration, SCYTHE delivers a unified approach to proactive defense.
Legacy BAS vendors may claim AEV capabilities, but their simulation-based, IOC-driven approach can’t keep pace with modern threats. SCYTHE’s focus on malicious behavior, multi-stage campaigns, and comprehensive metrics ensures organizations can validate controls, reduce risk, and stay ahead of adversaries.
Conclusion: Don’t Settle for Half-Measures
As CTEM becomes the gold standard for proactive cybersecurity, AEV is non-negotiable. Legacy BAS vendors, with their outdated architectures, can’t deliver the depth, realism, or metrics required for true AEV. SCYTHE’s adversarial emulation platform bridges the gap between theoretical testing and real-world resilience, empowering organizations to measure, improve, and prove their security posture. Don’t be swayed by rebranded BAS solutions—choose a platform that emulates the adversary, validates controls, and delivers results. Choose SCYTHE.
Latest Posts
Related Articles


The Future of Proactive Cybersecurity: Key Trends to Watch in 2025
In today’s cybersecurity landscape, standing still is not an option. Threat actors are becoming...

Michael Taggart's Journey in Education and Information Security
In this episode of the Phillip Wylie Show, hosted by SCYTHE Director of Services and Training, Phil...





