.png?width=1350&height=1350&name=Untitled%20design%20(14).png)
Redefining Proactive Security
Cyber threats evolve faster than traditional defenses. SCYTHE 5.0 changes the game with AI-powered adversarial exposure validation (AEV), built for security teams that need to know, not guess where they stand.
From on-prem to cloud-native environments, SCYTHE 5.0 enables continuous, intelligent, and mission-specific testing to ensure your defenses hold against today’s most advanced threats.
SCYTHE 5.0 introduces AI-powered automation, point-and-click functional testing, and rapid security stack integration, enabling continuous, real-world validation of cyber defenses in on-premise, cloud-native, and hybrid environments. This release empowers organizations to shift from static vulnerability scoring to dynamic, real-world threat validation, ensuring unparalleled preparedness against evolving cyber threats.
AI-Powered Campaign Builder
"My Ops" Visual Test Interface
Seamless Security Stack Integration
LLM-Driven Reporting
The SCYTHE Advantage
For Red Teams: Rapidly emulate real-world threats, organize TTPs, and automate campaign setup.
For Blue Teams: Validate controls continuously and detect gaps before they’re exploited.
For Purple Teams: Align red-blue collaboration with mapped exercises and auto-generated remediation insights.
For GRC: Map tests to compliance frameworks and auto-generate audit-ready documentation.
For CISOs & Risk Teams: Quantify threat risk, track improvements, and prove ROI on security spend.
Request Demo
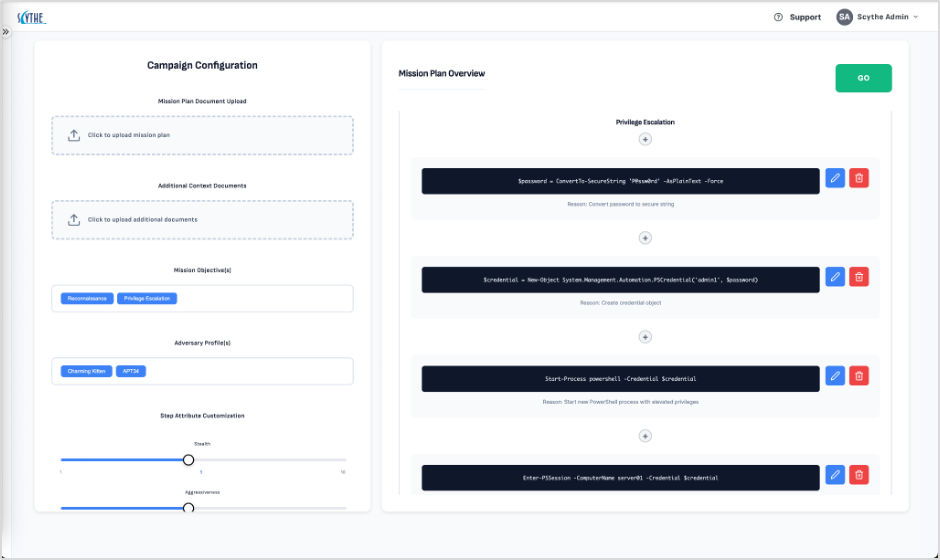
In a market saturated with tools that prioritize depth over usability—including SCYTHE's early versions—the platform now addresses the critical skills gap that has left mid-tier enterprises and overworked SOC analysts struggling with complex offensive security tools. By streamlining workflows into a "one-click" execution model complete with guided prompts, preconfigured templates, and automated infrastructure deployment, SCYTHE transforms episodic penetration testing into continuous, dynamic validation.The result is a comprehensive view of cyber posture that integrates threat insights, exposure preparedness, and control efficacy—all without the cognitive overload that has traditionally plagued these platforms. For security teams, this enables more frequent testing—weekly or even daily—without proportional increases in effort or expertise requirements.
SCYTHE's 2025 roadmap isn't merely refining a tool, it's redefining how organizations approach cybersecurity validation. By fusing AI-powered campaign building with user-centric UX design, it delivers immediate efficiency gains, broadens accessibility, and supports multifaceted security needs, from red, blue, and purple operations to GRC imperatives.
Latest Posts
Contact Us
Welcome to SCYTHE, your partner in understanding and defending against cyber attacks. We appreciate your interest in enhancing your cybersecurity defenses.
Please fill the form to reach out to our dedicated team.

