We're kicking off our first Threat Thursday of 2024 with two major threats. Up first is ALPHV/BlackCat, which was first unveiled at the end of 2023. Our second presentation is an update to LockBit (V3), which is garnering a lot of attention due to the discovery of numerous new behaviors.
About ALPHV/BlackCat
We have created a threat emulation plan based on the new Alphv BlackCat Variant. With this emulation plan, we have a new binary written in Rust that directly mimics the developer's intent for the BlackCat variant. This binary will undertake several actions seen in reporting for the BlackCat campaigns, including clearing and setting environment variables, targeted reconnaissance, impacting the system configuration in nine different ways, stopping ten services (same as seen in reporting) via the Windows API, and stops more than twenty processes before performing ransom actions and dropping the ransom note. It is an excellent example of the capabilities built into the real BlackCat ransomware campaigns and showcases a new age of sophistication on the horizon with malware development. Don't just take our word for it. Try it out and see if you can detect and alert on a variant such as Alphv/BlackCat.
About LockBit (V3)
In our comprehensive threat emulation plan for the latest LockBit 3.0 variant, we emulate the intricacies of this evolved ransomware. This emulation spans 8 tactics, encompassing over 15 techniques, each observed in recent LockBit 3.0 Ransomware attacks. What sets LockBit 3.0 apart is its heightened sophistication, leveraging advanced tactics like PowerShell execution, registry modifications, system enumeration, and data exfiltration. Furthermore, the ransomware's ability to encrypt both local and remote systems, as well as terminate services and processes, amplifies its overall impact. If you're serious about cybersecurity, explore our threat emulation plan. It's a unique opportunity to delve into the intricacies of LockBit 3.0 and fortify your defenses against this advanced ransomware variant!
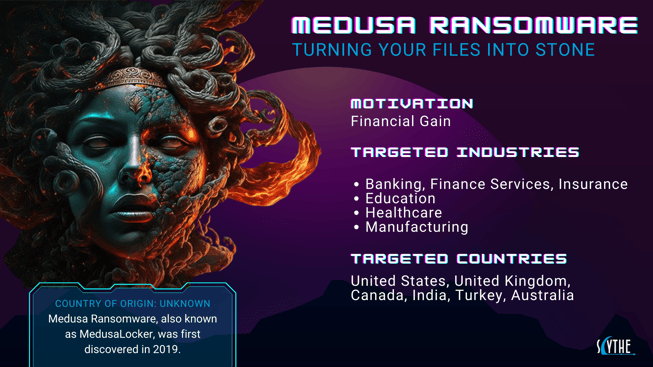
We're thrilled to unveil our latest threat emulation plan designed to combat the infamous Medusa Ransomware!
✅ Key Features
Detections: Our dedicated team at SCYTHE Professional Services has provided advanced detections for proactive defense against potential Medusa threats.
Comprehensive Emulation: Stay one step ahead with our thorough Empower IOC plan.
🔎 About Medusa Ransomware
Medusa is a formidable ransomware known for its sophisticated encryption techniques. It preys on vulnerabilities, encrypts files, and demands a ransom for decryption keys.
🔓 Stay Protected, Stay Secure
Don't let Medusa strike! Upgrade your defense today and experience peace of mind.
Jan. 23 Free Virtual Workshop - Threat Emulation Engineering
Register today! Our debut Threat Emulation Engineering workshop is designed to mimic real-world threats to help organizations improve incident response, enhance security measures & ensure effective controls are in place. Take advantage of our next free virtual session with Lead Adversary Emulation Engineer Trey Bilbrey on January 23 from 2-3 PM (ET).
About the Author
Trey Bilbrey is a Lead Adversary Emulation Engineer at SCYTHE, specializing in Purple Team Exercises, Threat Emulation, Critical Infrastructure, and holistic cyber operations. Trey's 15 years of industry experience has allowed him to become an excellent educator, defender of networks, and a cultivator of cybersecurity professionals. Prior to joining SCYTHE, Trey held positions at notable organizations such as Hack The Box (HTB Academy content Developer), The Army Corps of Engineers (ICS/SCADA Penetration Testing), and a veteran of the United States Marine Corps ( Defensive and Offensive Cyber Operations). Current certifications include the CISSP, GICSP, GCIP, and K>FiveFour RTAC.
About SCYTHE
SCYTHE represents a paradigm shift in cybersecurity risk management, empowering organizations to Attack, Detect, and Respond efficiently. The SCYTHE platform enables collaboration between red, blue, and purple teams to build and emulate real-world adversarial campaigns. SCYTHE's innovative dual-deployment options and comprehensive features ensure a proactive cybersecurity approach. Headquartered in Arlington, VA, SCYTHE is privately funded by distinguished partners dedicated to shaping a more resilient cybersecurity landscape.











