This edition of Threat Thursday is buzzing with a few highlights from the cyber realm during the 4th quarter of 2023. In particular, we want to spotlight Microsoft's Digital Defense Report and the release of Version 14 for MITRE ATT&CK.
Microsoft's Digital Defense Report 2023
MDDR 2023 is the fourth annual release Microsoft has provided to the cyber community, highlighting the state of cybersecurity, the threats we face, and a look to the future.
SCYTHE Insights
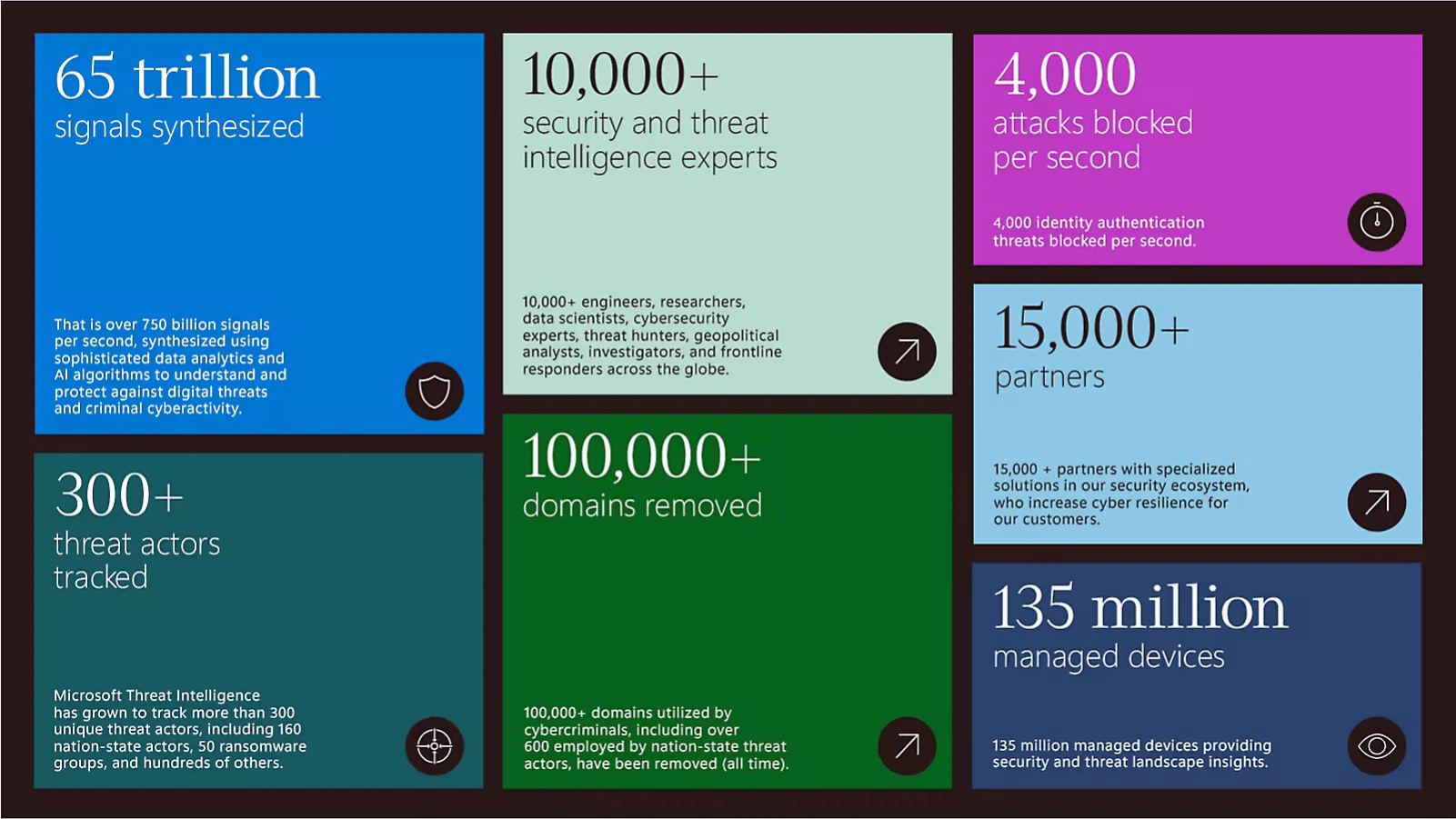
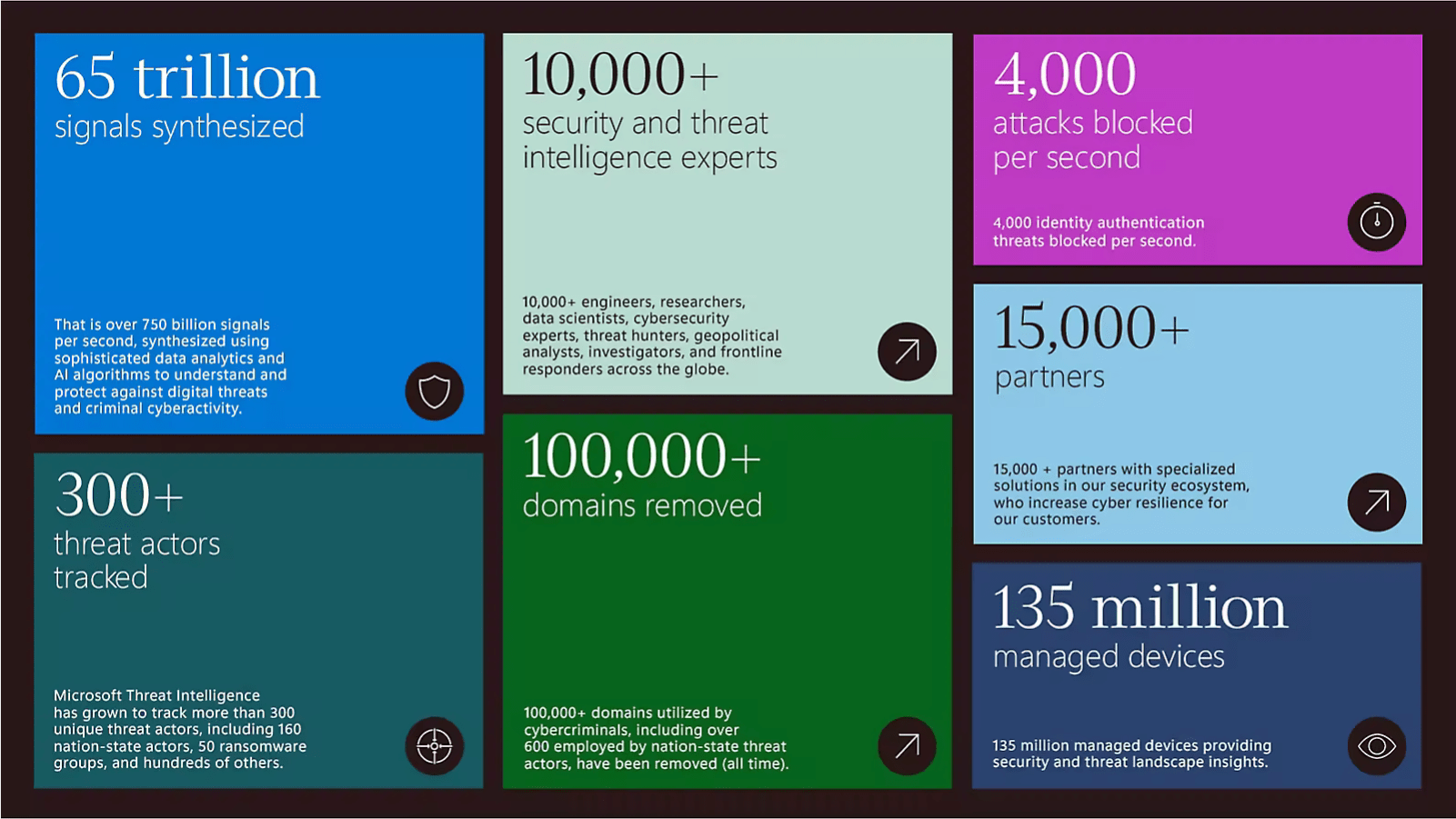
This year's Digital Defense Report is an extensive and exceptionally well-curated look into the state of Cybersecurity through 2023. Microsoft has provided great insight through their data sources and CTI into this year's most prolific threats, cybercrime, continuous and new challenges we are all facing, and innovation leaps in defense that happened through 2023. It is worth a read, especially the section detailing Nation State actions. The image below shows just a few of the insights provided by Microsoft's team.
Sources
https://www.microsoft.com/en-us/security/security-insider/microsoft-digital-defense-report-2023
MITRE ATT&CK® Update (V14)
MITRE ATT&CK® is our trusty resource for all things threat mapping and helps provide practitioners the world over with a central resource for understanding threats, the techniques they use, and how to detect and respond to them.
SCYTHE Insights
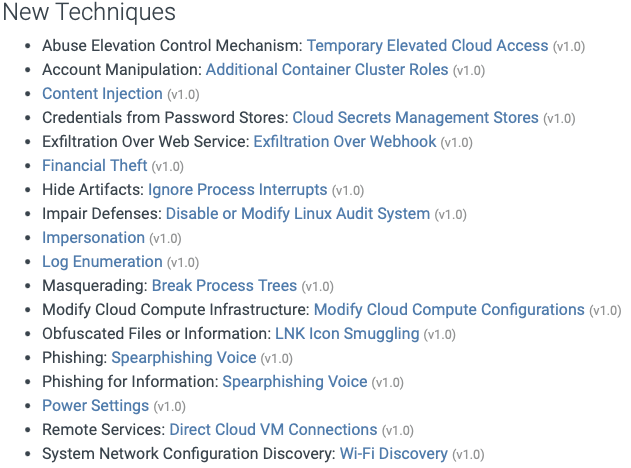
At the end of October 2023, ATT&CK® released an update (V14) to the framework, introducing many changes to Techniques, Groups, Campaigns, and Software for Enterprise, Mobile, and ICS. This update improves the usability of the Changelog, introduces many new and revised techniques, and dramatically expands the detection notes and analytics sources accompanying each TTP. We are excited about the addition of Assets to the ICS mappings and how it will improve the inclusion of OT assets into the cyber discussion with common definitions and specific technique relationships. The image below outlines just some of the new technique additions to the Enterprise mappings!
Sources
https://attack.mitre.org/resources/updates/
attack-v14-fa473603f86b
Upcoming Workshop - Detection Engineering
Register today! Learn the detection engineering process in this FREE three-hour workshop with Principal Detection Engineer Chris Peacock. After going over each step of the cycle, we will dive into a hands-on workshop to put the method to practical use.
About the Author
Trey Bilbrey is a Lead Adversary Emulation Engineer at SCYTHE, specializing in Purple Team Exercises, Threat Emulation, Critical Infrastructure, and holistic cyber operations. Trey's 15 years of industry experience has allowed him to become an excellent educator, defender of networks, and a cultivator of cybersecurity professionals. Prior to joining SCYTHE, Trey held positions at notable organizations such as Hack The Box (HTB Academy content Developer), The Army Corps of Engineers (ICS/SCADA Penetration Testing), and a veteran of the United States Marine Corps ( Defensive and Offensive Cyber Operations). Current certifications include the CISSP, GICSP, GCIP, and K>FiveFour RTAC.
About SCYTHE
SCYTHE represents a paradigm shift in cybersecurity risk management, empowering organizations to Attack, Detect, and Respond efficiently. The SCYTHE platform enables collaboration between red, blue, and purple teams to build and emulate real-world adversarial campaigns. SCYTHE's innovative dual-deployment options and comprehensive features ensure a proactive cybersecurity approach. Headquartered in Arlington, VA, SCYTHE is privately funded by distinguished partners dedicated to shaping a more resilient cybersecurity landscape.
.png?width=352&name=60cb5721a99a19ede064a336_NOBELIUM%20(6).png)