This joke highlights key differences between Information Technology (IT) and Operational Technology (OT) in Industrial Control Systems (ICS). ICS devices are typically purpose-built for specific tasks, expected to be highly reliable and safe, with an expected long lifecycle, often spanning decades. Because of this focus on high availability (meaning in service all the time), patching and updating these systems are infrequent or sometimes impossible due to the risks of disrupting critical operations. Traditional endpoint security tools often face limitations in these environments.
The priorities in OT environments also differ significantly from IT. While IT focuses on the principles of confidentiality, integrity, and security, OT systems emphasize safety, availability, and revenue protection. This means that ensuring the physical safety of systems and maintaining their uninterrupted operation are paramount. Any disruptions can have significant financial impacts or, worse, endanger human lives, making the OT domain uniquely challenging compared to IT.
Additionally, the inability to easily patch or update OT systems increases their vulnerability to modern threats, requiring specialized security measures and strategies to protect these legacy systems effectively. As a result, securing ICS demands a different approach, blending traditional cybersecurity practices with a deep understanding of industrial processes and their associated risks.
Architectural Summary: IT vs. OT Networks
IT Network Architecture:
• Purpose: Primarily focused on information management, data processing, and business operations.
• Structure: Typically has a flat, interconnected structure where devices and users access applications, data storage, and cloud services through centralized servers.
• Security Priorities: This policy emphasizes confidentiality, integrity, and security and strongly focuses on data protection, access control, and regular patching.
• Components: Includes servers, workstations, cloud services, routers, switches, and security devices (e.g., firewalls, IDS/IPS).
OT Network Architecture:
• Purpose: Focuses on controlling and monitoring physical processes, machinery, and industrial operations (e.g., SCADA systems, PLCs).
• Structure: Hierarchical and segmented architecture (often following the Purdue Model and/or ISA/IEC 62443) with distinct layers for control systems, safety systems, and physical processes. Segmentation helps protect critical systems from threats.
• Security Priorities: Safety, availability, and reliability are prioritized over confidentiality. Patching and system updates are infrequent due to the need for continuous operation.
• Components: Includes field devices (sensors, actuators), controllers (PLCs, RTUs), Human-Machine Interfaces (HMIs), and supervisory systems (SCADA). Many devices are purpose-built with long life cycles. We have seen a blended environment with COTS appliances/systems as well.
Comparison:
- Interconnectedness: IT networks are more interconnected, facilitating data flow, while OT networks are segmented to isolate critical systems.
- Security Focus: IT prioritizes data protection; OT prioritizes operational continuity and safety.
- Patching: IT frequently updates systems; OT rarely patches due to potential disruption to critical processes.
- Device Lifecycle:** IT devices have shorter lifespans and faster replacement cycles, whereas OT devices are built to last for decades.
Understanding these architectural differences is crucial for organizations aiming to secure both their IT and OT environments effectively.
The Purdue Model is a reference architecture that helps organize and secure Industrial Control Systems (ICS) and Operational Technology (OT) networks. Developed in the 1990s, it breaks down ICS/OT networks into five levels, each representing different functionalities and security needs, ranging from physical processes at the lowest level to enterprise network management at the highest. The model helps illustrate the value of segmentation (control zones), conduits (communication systems), and understanding of different operational layer relationships, helping organizations effectively manage and secure their OT environments by defining where certain security controls and network protocols should be applied.
Purdue Model

Approach, Priorities, and Wins
Establishing trust with OT engineers is essential and requires security teams to align with the unique priorities of OT/ICS personnel—namely safety, operational availability, and reliability. Security professionals should start by asking OT engineers directly about their priorities and concerns.
Two practical areas to initiate collaboration include:
- Business Continuity Planning/Disaster Recovery: OT teams are already well-versed in this area. The convergence of IT and OT environments introduces new threats, like ransomware, that directly target operational disruptions. By integrating security measures into existing continuity plans, security teams can align their efforts with the existing goals of OT engineers.
- Remote Access Management: OT environments often involve third-party vendors with contractual access to devices for diagnostics and updates. Collaborating on securing remote access can result in immediate operational benefits, aligning security with the critical need for availability.
To effectively engage with OT teams, security professionals must first build trust—starting with open communication, demonstrating the reliability of security tools, and establishing transparent processes.
The Purple Teaming approach is exceptionally beneficial in OT/ICS environments as it bridges the gap between IT security and OT engineering teams. This method promotes a collaborative environment where both groups work together to enhance security without compromising operational priorities. By emphasizing shared goals, such as safety and operational continuity, Purple Teaming fosters transparency in threat emulation exercises, ensuring that security measures align with the unique needs of OT systems.
This collaboration strengthens the overall security posture and builds mutual trust, leading to more effective and efficient remediation efforts. Additionally, it ensures that security practices are tailored to the specific requirements of both IT and OT environments, thereby reducing the risk of operational disruptions while enhancing the organization’s ability to defend against sophisticated cyber threats.
IT environments are the most common initial access vector for cyber threats due to their inherent exposure to the internet, a necessity for conducting business. This makes them the largest surface area for attackers to target. Once a threat actor gains entry into the IT environment, they typically engage in iterative reconnaissance and attempt lateral movement toward the OT environment to gain a beachhead which collapses the illusion of defense in depth of Purdue. This phase presents a critical opportunity for organizations to detect and respond to threats before they reach critical OT systems.

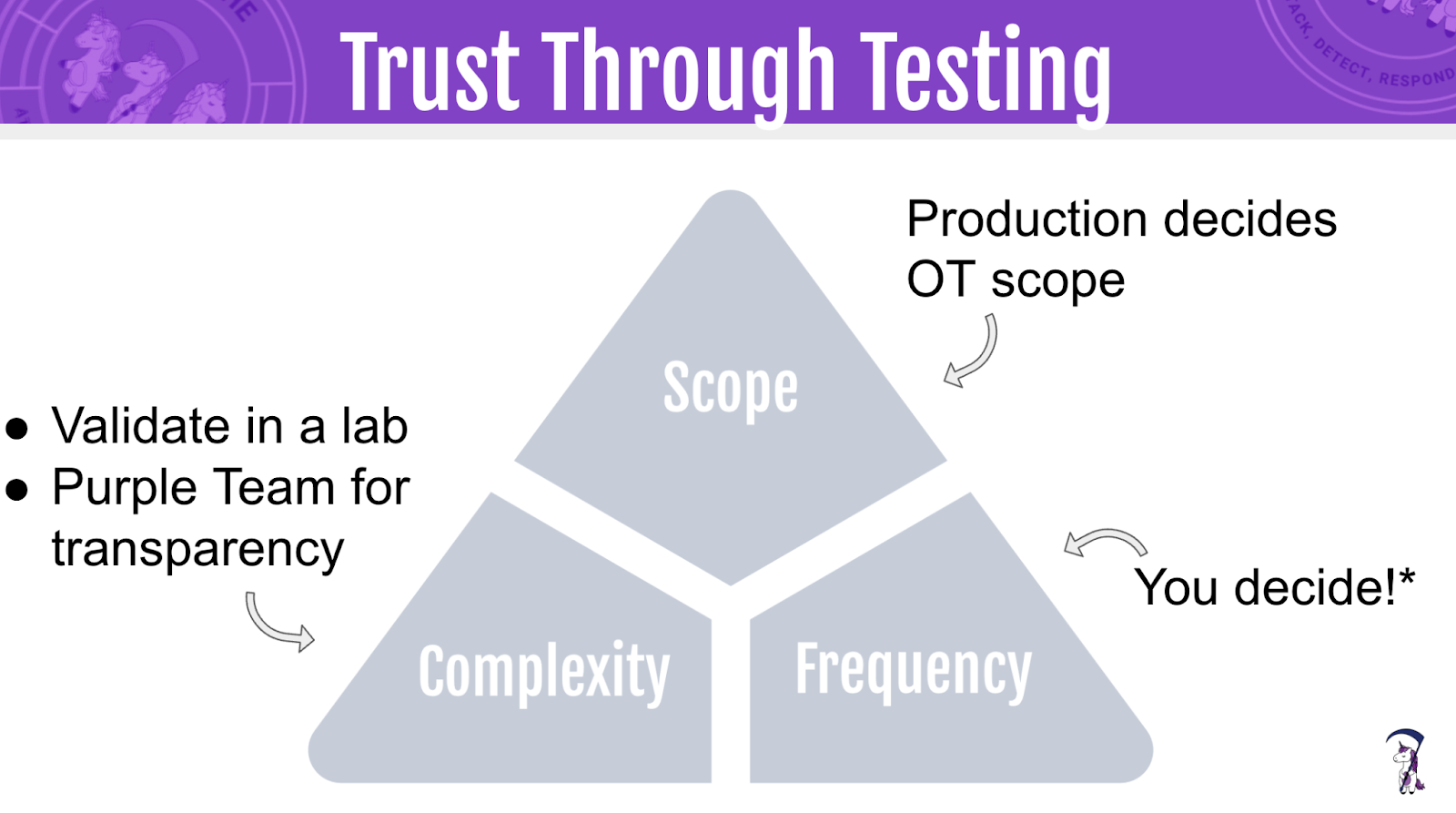
To effectively protect OT environments, it's essential to "build toward OT" by understanding and addressing three core pillars: scope, frequency, and complexity.
- Scope: This involves defining the boundaries and extent of security measures ensuring comprehensive coverage of all potential attack vectors that could be exploited to bridge IT and OT systems.
- Frequency: This refers to the regularity with which security assessments, testing, and monitoring are conducted. Frequent evaluation helps in identifying new vulnerabilities and understanding evolving threat landscapes.
- Complexity: OT environments often have complex, interconnected systems with unique operational requirements. Teams need to analyze and manage this complexity by developing detailed, tailored security plans that account for the intricacies of OT systems while ensuring that any security implementations do not disrupt critical operations.
By focusing on these pillars, organizations can create robust strategies that prevent threats from moving laterally from IT to OT, safeguarding critical infrastructure from potential cyber-attacks.
.png?width=352&name=60f5db5cfc0fb50b50f1de12_Beachhead%20Access%20in%20Industrial%20Control%20Systems%20(2).png)